Mastercard Cybersecurity Virtual Experience Program

I decided to do the Mastercard Cybersecurity Virtual Experience Program. This program is made up of two tasks. During the first task, I will have to examine an obvious fake email and make it more believable. For the second task, I will have to create a short presentation to help teams improve security awareness.
Task 1
You are an analyst in our Security Awareness Team.
Our Chief Security Officer (CSO) relies on our team to help our staff learn how to identify and report security threats to Mastercard.
One of the most common threats organizations face today is phishing. So, what is phishing?
- Phishing is the act of pretending to be someone/something to get information, in most cases, this is usually a password.
- Attackers may send links or attachments designed to infect the recipient's system with malicious software or lure them into providing financial information, system credentials or other sensitive data.
- Successful phishing attempts can cost companies like Mastercard millions of dollars and put our employees at risk. So it’s very important that we keep the business and our staff safe from harm.
At Mastercard, one of the ways we mitigate phishing threats is by educating our people about the risks and how to identify them. An effective way to build awareness is through phishing simulation campaigns:
- We test our staff every month by sending a fake phishing email that is made to look like something a bad actor would send.
- We use the results of the simulated test to help us design and implement future training.
What can a phishing email look like?
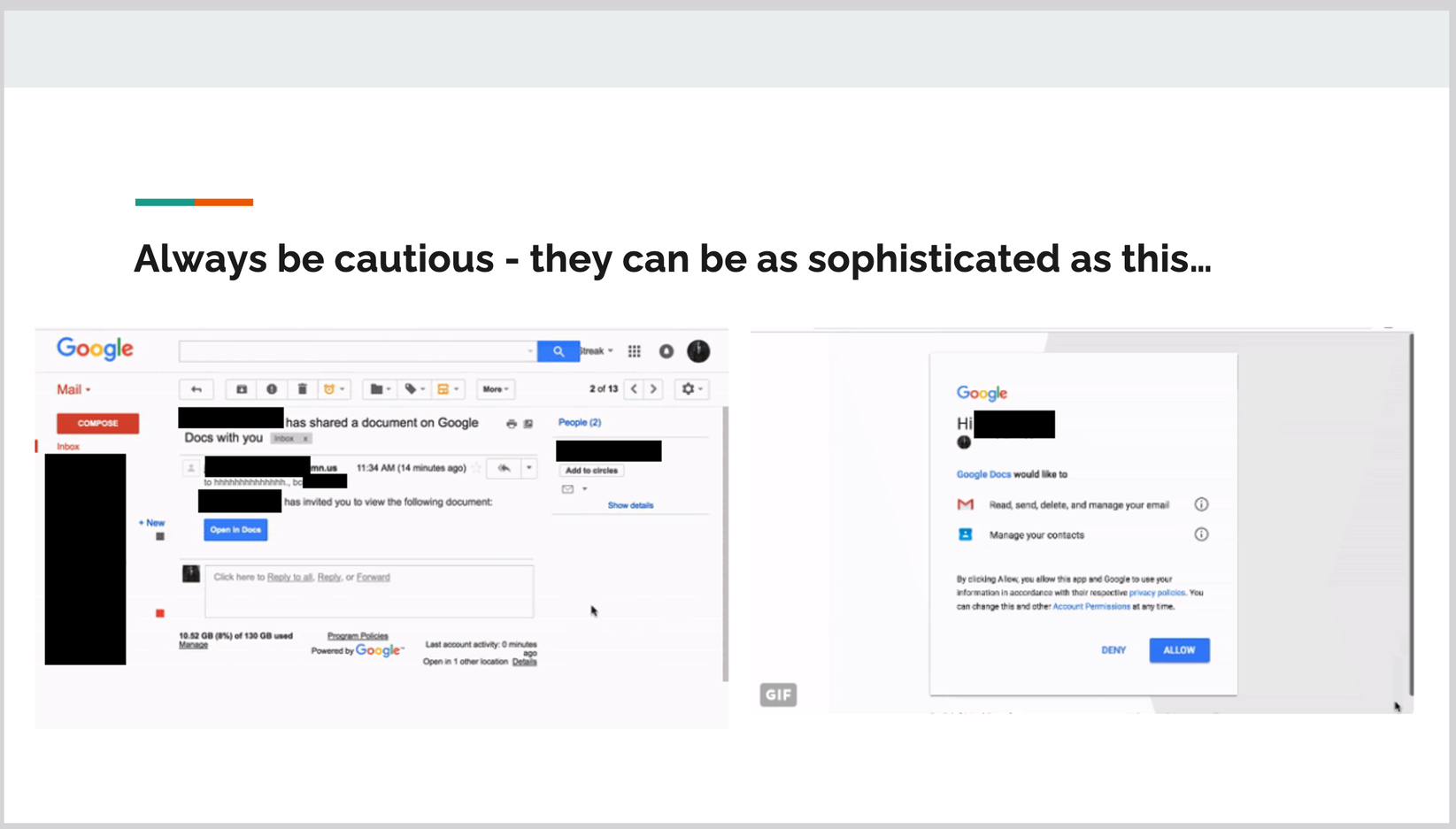
A few months back, we detected a phishing email that was being used by an external bad actor on some of our employees.
Thankfully, it failed due to being an obvious fake. However, we know that phishing emails are now getting very sophisticated and a range of tactics are used.
Start the quick quiz to learn what an ‘obvious fake’ might look like.
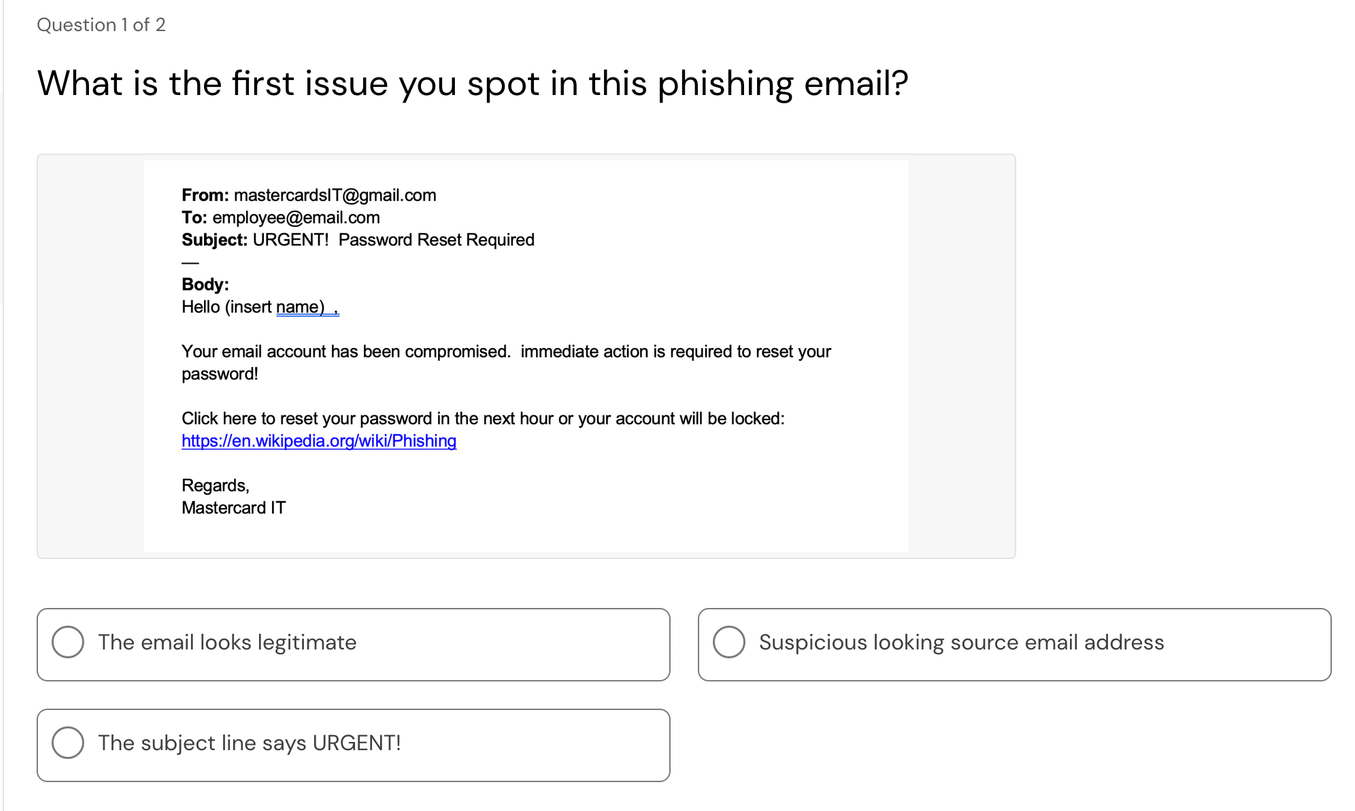
The obvious thing to spot in this first question in the source email address, 'mastercardsIT@gmail.com'. It is highly unlikely that Mastercard would send an email from a gmail domain. You would be far more like to receive an email from *@mastercard.com.
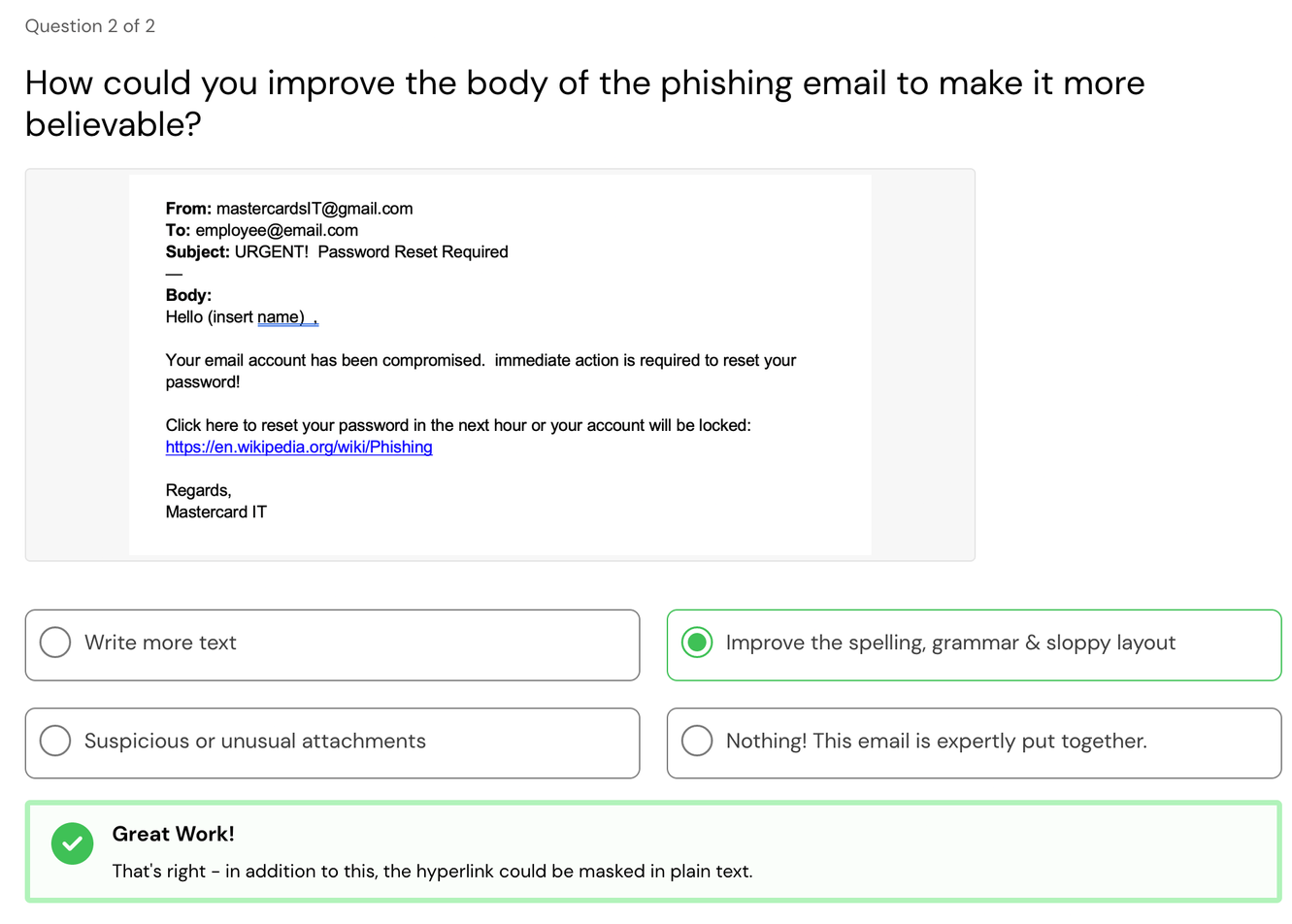
A big concern for me is the body saying 'Hello (insert name) ,' but then you can also see 'compromised. immediate' which gives us the answer, which you can see above.
Next up, improve the phishing email.
Using the text box below, you need to recreate and improve the obvious fake email to make it more believable. Remember the end goal is to encourage the user to click on the link.
To create a ‘good’ phishing email, you should:
- Add some context at the beginning - make it relevant to a Mastercard employee
- Mask the hyperlink within text
- Use correct spelling and grammar
- Add points of legitimacy
Once you've submitted your email, we'll show you an example of a good phishing email.
Here is the obvious fake:
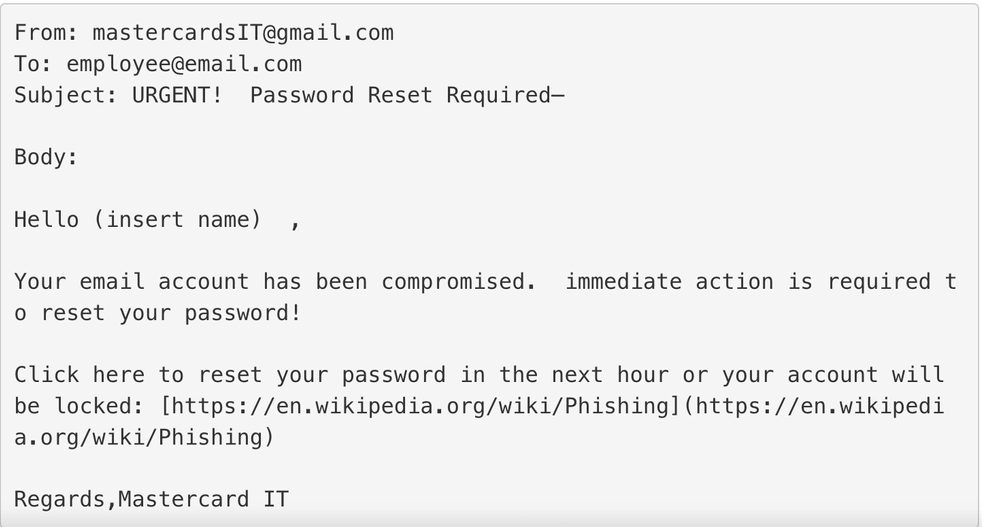
There are a few things, I would change:
1) Source email address - you could spoof this, but even trying to use a cyrillic 'a' instead of a latin 'a' when registering your 'mastercard' domain.
2) I would calm down the email subject. Although, it is urgent, personally, I think that the 'URGENT' makes it fishy. Something like 'Account Compromise' is slightly more professional.
3) Remove 'Body:', address the individual and clean up the body. Within, the body content clean up, I have included the Mastercard IT team contact number, which I may have found through some social engineering. Giving the option to call the team gives a false sense of security to the target. It's likely they will choose to click the link to our phishing site to save having to talk to the IT team and just to get on with it themselves.
4) The phishing link could also be a "Mastercard domain" with a link to a seperate site.
This is my improved phising email:
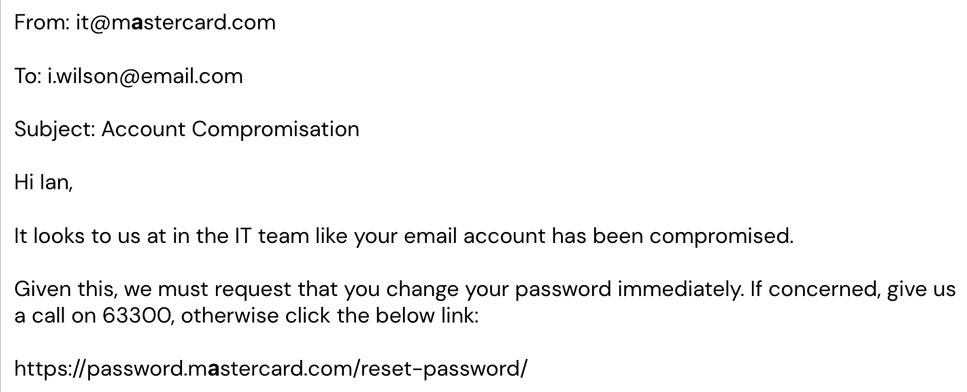

Here you can see the improved version from Mastercard

There are many ways you can change the email. I kept my email along the same tracks of an account compromise, but you can see above that this email is enticing as it is an 'Employee reward card'. I do like the addition of the confidentiality disclaimer to increase email legitimacy.
Task 2
It's time to identify and train your teams.
The phishing simulation designed in the first task was run last week. So, what’s next?
We’ve used some tools to analyze the results and we can see the failure rate of each department - it is clear that some teams appear more likely to fall for a phishing email than others.
Now that we have these results, we need to:
- identify which areas of the business need more awareness about phishing, and
- design and implement the appropriate training for those teams to lower our risk of an attack.
Interpret the results
First, let’s have a look at the results of the phishing campaign.
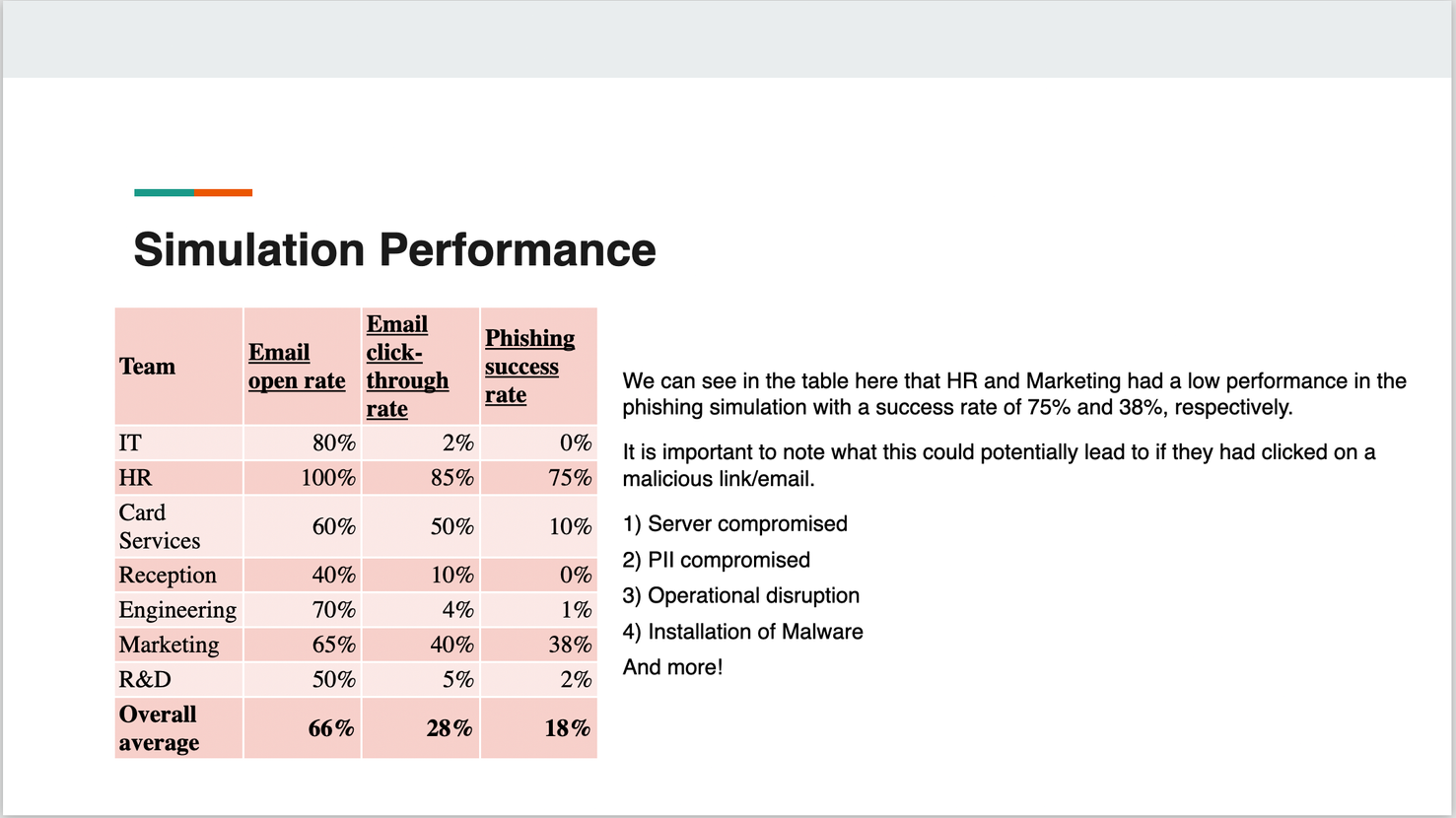
This table helps you to identify which teams appear to be more likely to fall for a phishing email than others.
| Team | Email open rate | Email click-through rate | Phishing success rate |
| IT | 80% | 2% | 0% |
| HR | 100% | 85% | 75% |
| Card Services | 60% | 50% | 10% |
| Reception | 40% | 10% | 0% |
| Engineering | 70% | 4% | 1% |
| Marketing | 65% | 40% | 38% |
| R&D | 50% | 5% | 2% |
| Overall average | 66% | 28% | 18% |
When you’re ready, start the quick quiz to see if you’ve correctly identified the most vulnerable teams.
Here are some resources to help you
The percentages shown are based off the total number of staff members who received the email.
For example if 100 people received the email and 50 people opened it - the email open rate would be 50%.
- Email open rate = the percentage of people that opened it
- Email click-through rate = the percentage of people that clicked on the link
- Phishing success rate = the percentage of people that clicked the link and inputted some personal information
Let's start the quiz.
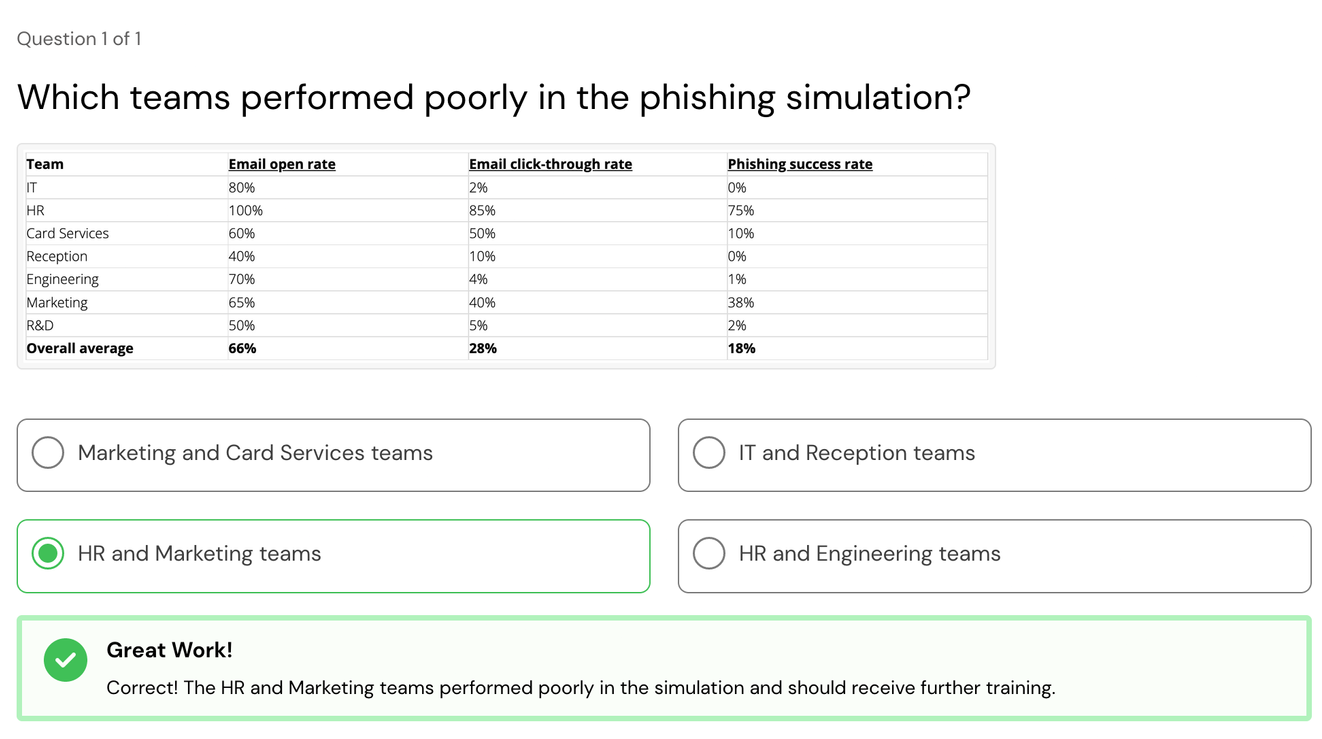
Here, we can see the phishing success rate was highest within the HR and Marketing teams, which shows they performed poorly in the phishing simulation.
Create a short presentation
Now that you've analyzed the results, it's time to create a short presentation (3-5 slides) providing some awareness and training materials for the two teams that appear to be most susceptible. This will help us improve the security awareness of the teams that performed poorly in this campaign.
I ended up creating a presentation, which briefly shows the two teams who are most susceptible to phishing but then speaks to every team within the company, explains the dangers of phishing and what to keep an eye out for.
Here is my presentation in images:
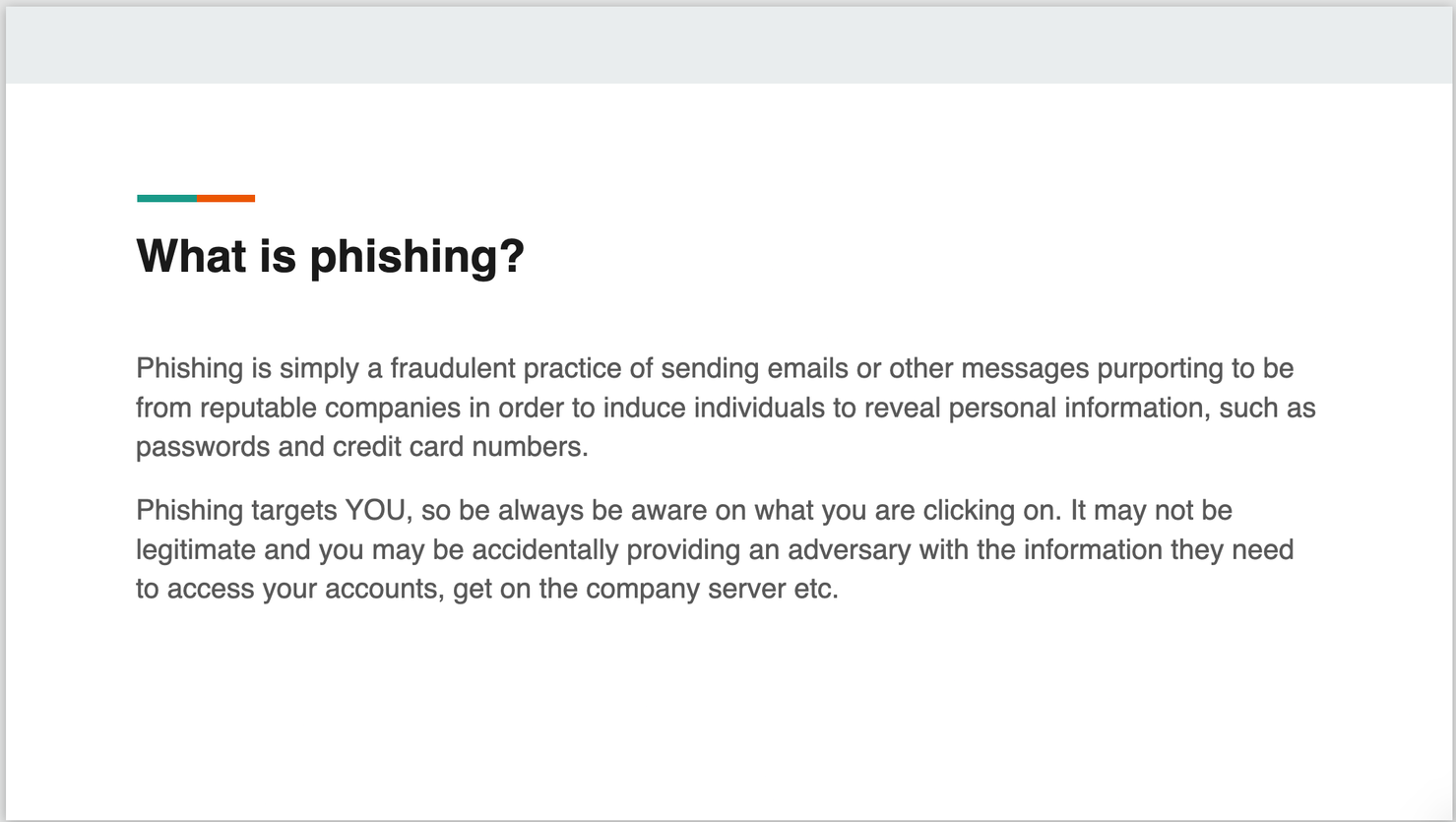
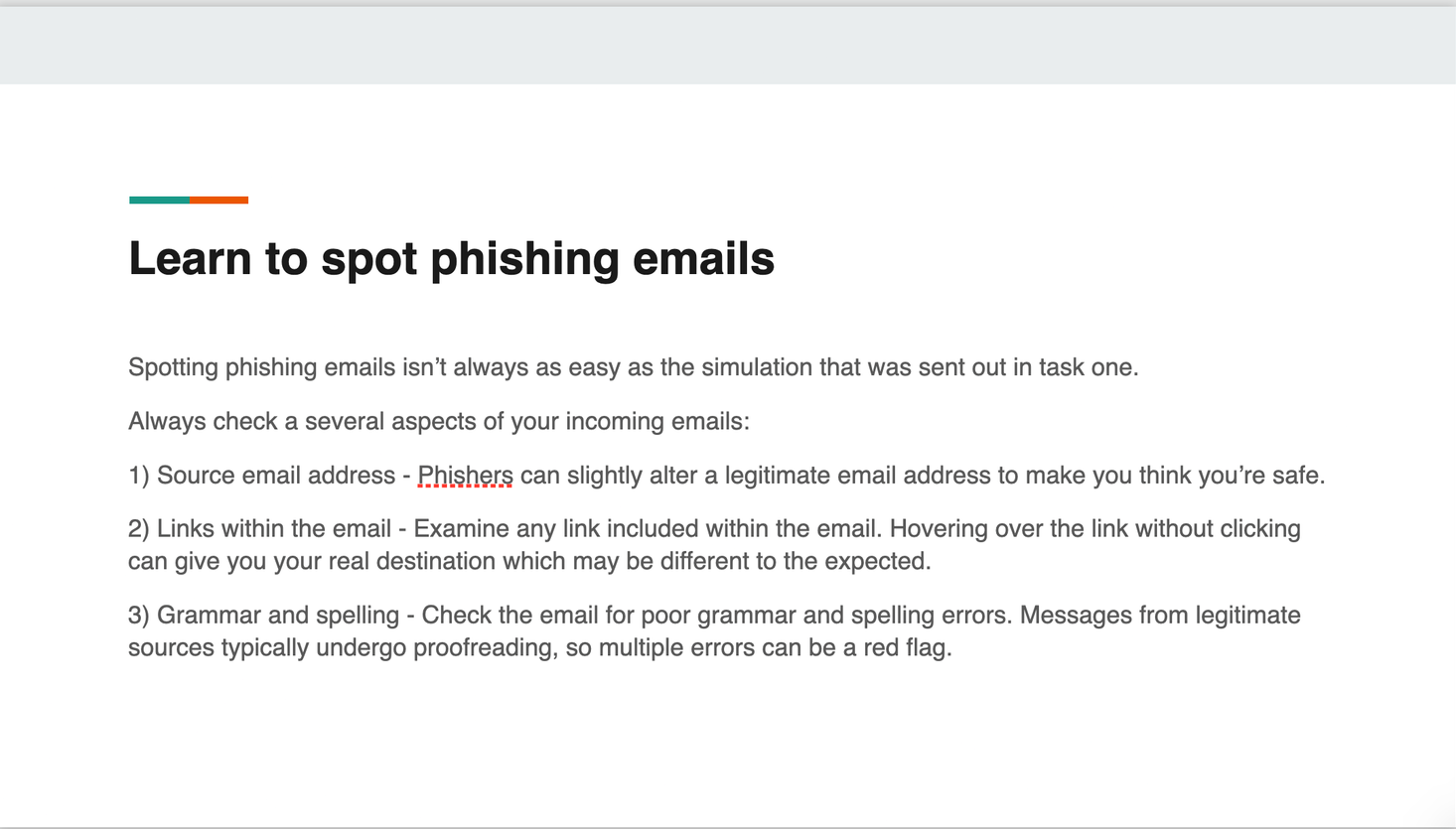
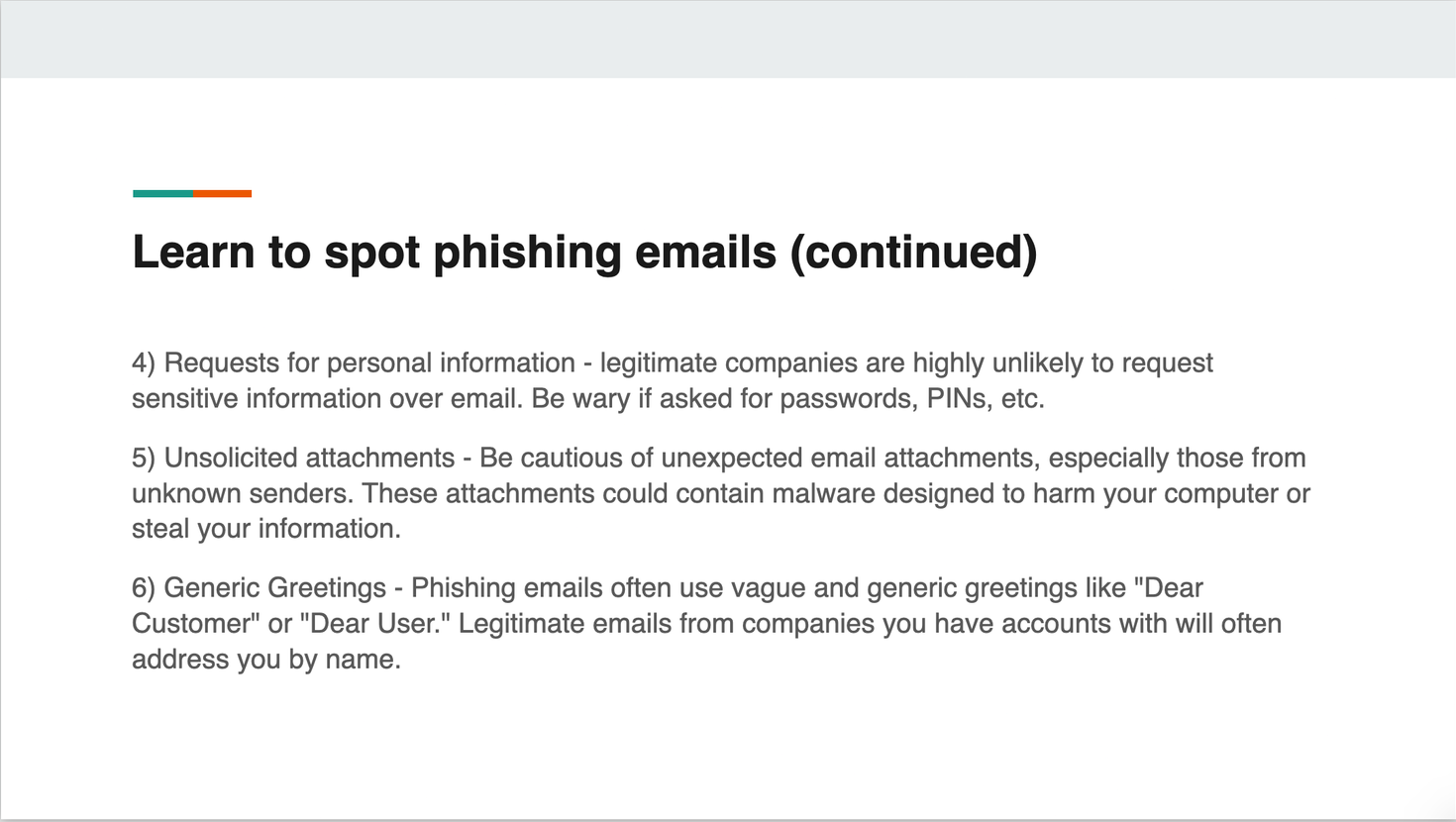
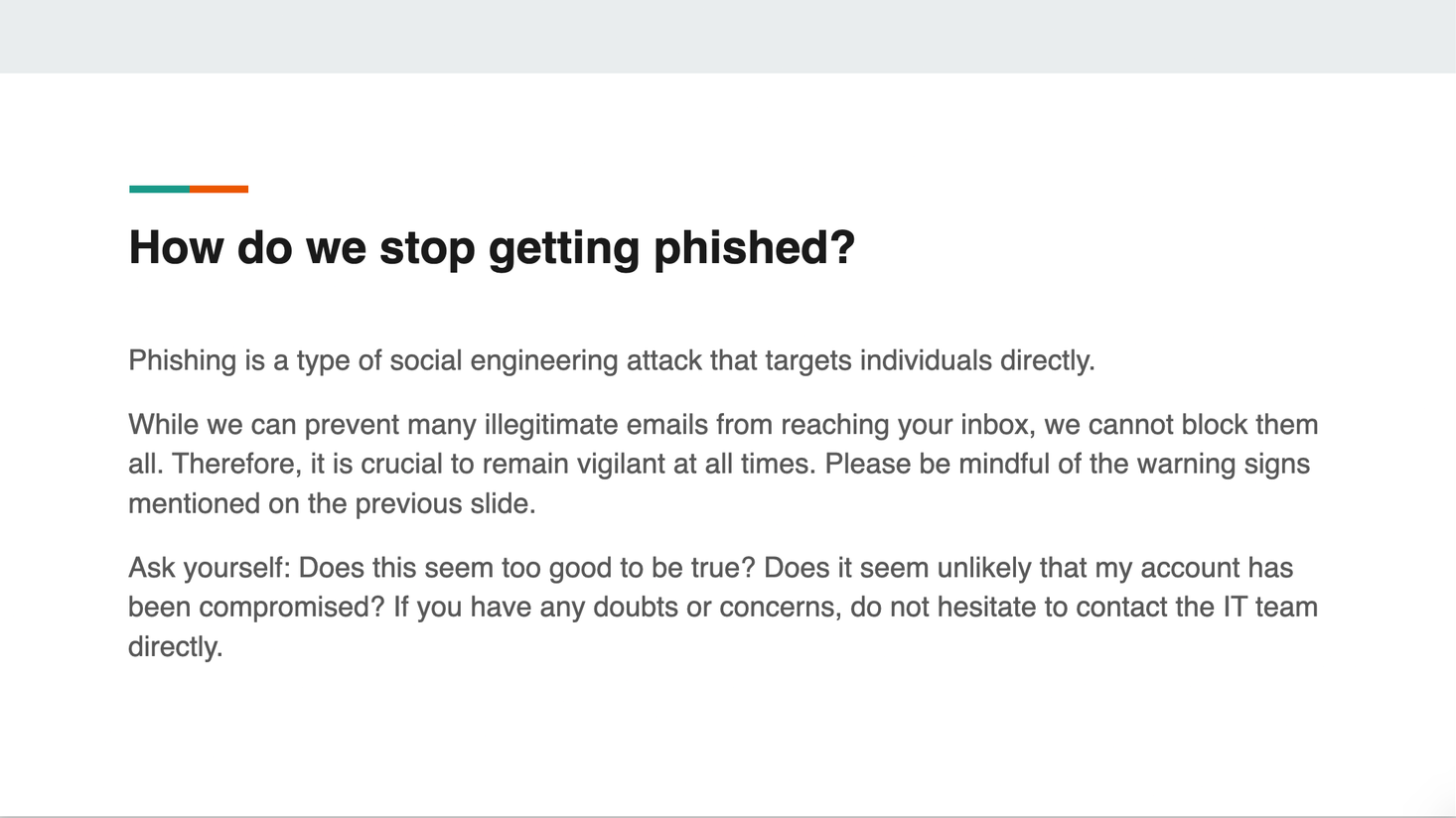
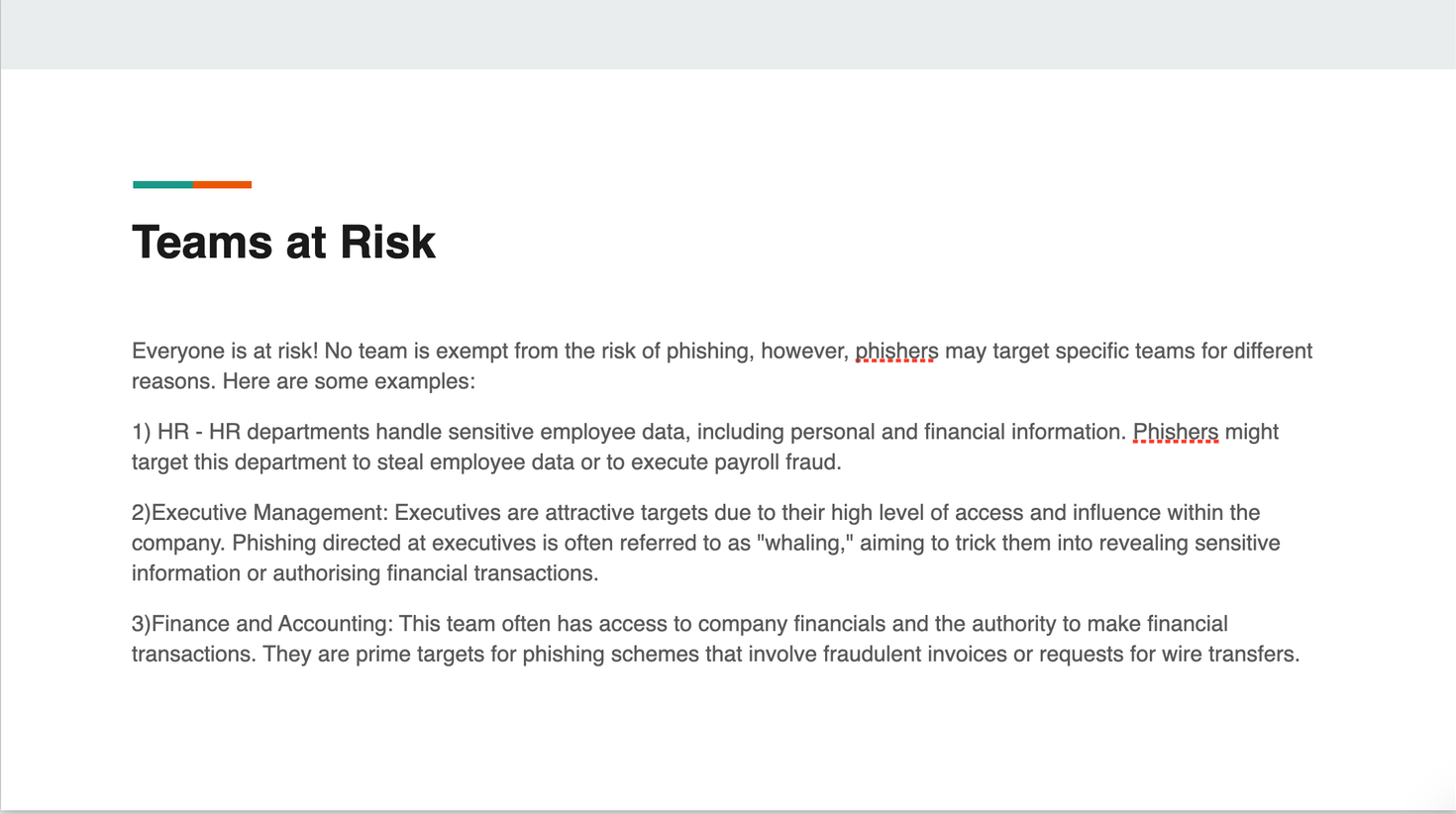
I ended up doing a presentation of 7 slides. I believe my presentation covers all the necessary aspects, emphasizing that everyone is at risk and highlighting the notion that the target is 'YOU'—meaning anyone within the organization.
Looking through the example presentation from Mastercard - the key thing I missed is examples of phishing attacks (see below).