I wrote a keylogger with Python

Out of curiosity, I wanted to write a keylogger, and I knew that one man (LLM) who could help me was ChatGPT.
N.B. This script was created solely for educational purposes to explore the functionality of input monitoring. It is essential to ensure that such tools are used responsibly and ethically. Unauthorised use of keyloggers can lead to legal and ethical issues.
I started by inputting a few different prompts into ChatGPT and received an initial keylogger script written in Python, using the keyboard import from PynPut. This library allows for controlling and monitoring input devices, currently supporting mouse and keyboard input.
While working in VS Code, I was ready to run the code when I noticed a couple of pop-ups in the bottom corner of my system.
The instant removal of my initial keylogger was impressive. It meant that the security service in place was actively removing potentially malicious files, even while I was working on them. This observation led me to think about possible workarounds, such as the use of Base64 encoding to obfuscate.
I proceeded to encode the script in Base64 using CyberChef.
Then, with ChatGPT's assistance, I created a script to decode and execute the Base64-encoded variable. I quickly resolved a NameError that initially appeared, which was due to the keyboard import only sitting in the Base64 code, not the main python file.
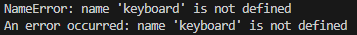
However, the script wasn't detecting any key entries.
I'd execute the code and then nothing would register until clicking 'Esc'. To troubleshoot, I reviewed the Pynput documentation and identified a few discrepancies. After making the necessary adjustments, I executed the final code, which included the Base64 variable.
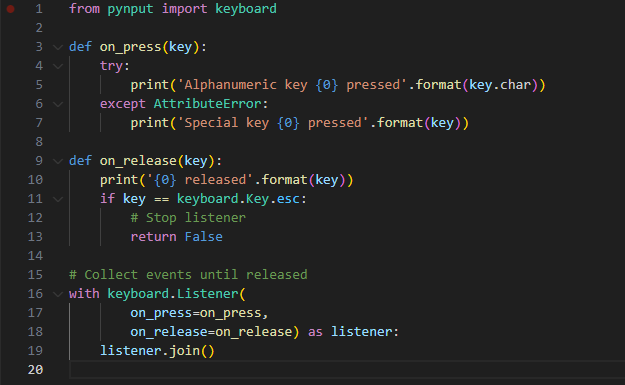

And, as we can see here, when inputting 'hello' into a word document, each key entry was recorded.
This is a basic outline of a keylogger. An adversary may obfuscate the process by integrating the keylogger into an application, which could involve converting the code to C++ and injecting it into a .dll file. Additionally, the adversary might inject the keylogger into the system’s run keys to ensure persistence, meaning the keylogger will automatically start whenever the specific machine or user is online. The script is then configured to report to a command-and-control (C2) server. The log file (e.g., log.txt) contains everything typed within the last 5, 15, or 60 minutes, depending on how frequently the script communicates with the server.