I set up Aftermath on my Mac OS

On Sunday afternoon, I found myself reading a paper on 'Rapid Incident Response on macOS: Actionable Insights in Under an Hour'[1], within which, Doug Hitchen mentioned the user of Aftermath, a Swift-based open-source IR tool for Mac OS.
This instantly piqued my interest as I have used Mac OS for my whole life, however, with the security market being held by Windows at 89% in 2014 (StatCounter, 2014), I never felt like there was much available within Mac OS similar to this. I have known about Jamf for a while, but this as previously mentioned piqued my interest. Another great statistic that I read about was the increase in Mac usage. In the past decade, this has increased from 8.5% to almost 15% (StatCounter, 2014 and StatCounter, 2024).
So, my next move was to set up Aftermath. The details on the setup can be found on Github at [https://github.com/jamf/aftermath].
What is Aftermath?
Aftermath is a Swift-based, open-source incident response framework.
Aftermath can be leveraged by defenders in order to collect and subsequently analyse the data from the compromised host. Aftermath can be deployed from an MDM (ideally), but it can also run independently from the infected user's command line.
How do I plan to use Aftermath?
While Aftermath is an IR tool, I have no current incidents to respond to. Therefore, my thoughts with Aftermath are to leverage it in a proactive manner for ongoing security monitoring and early threat detection on my macOS system.
This pro-activity will include
- Scheduled Scans (in order to check if there are any changes and perhaps catch an emerging threat)
- Baseline System State (understand how my machine looks prior to any future incidents)
- Real-time Alerts (perhaps through integration with a SIEM)
- Pre-emptive Configuration Audits (to see best practices)
- Detecting Known Threats and Malware (checking against known IoCs)
- Correlating with External Threat Intelligence (to assist with the above)
I think understanding a variety of OS's is extremely important in a world where the surface is ever changing. My understanding of Linux and Windows are coming along nicely when it comes to the fundamentals, however, my knowledge of the MacOS security base is definitely limited even though I have used it for most of my years.
The Setup
The setup was a rather simple one as you will see from the below images. The GitHub repo (link is above) directed me to complete the setup and has the log files output.
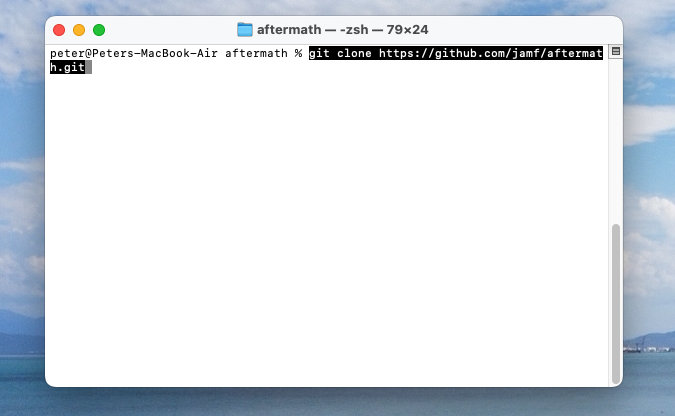
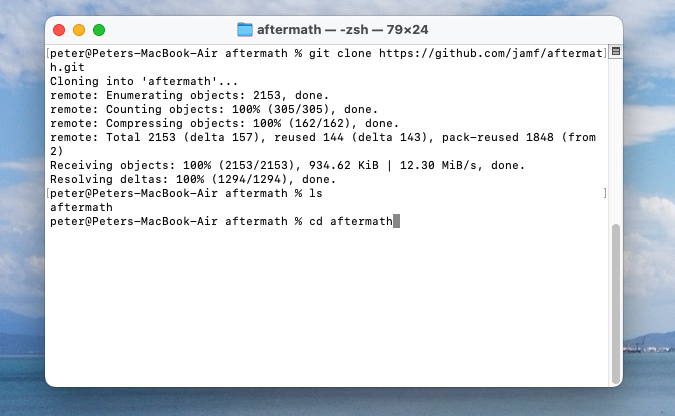
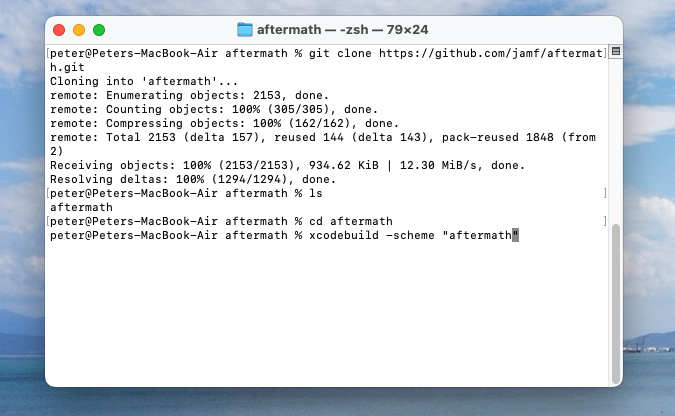
At this point I ran into some errors where I didn't have the CLI correctly installed. However, after some light troubleshooting, I was able to complete the build as seen below. Once I had the correct CLI installed, I then hit some certificate signing issues. Again, this required some minor troubleshooting and I had to ensure the 'Automatically manage signing' checkbox within the 'Signing & Capabilities' tab of the 'Aftermath' target was checked.
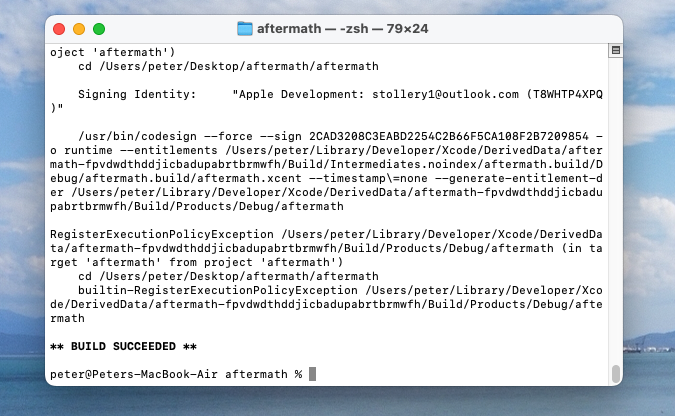
Having run Aftermath, I was provided with a few varying folders within which there were log/text documents.
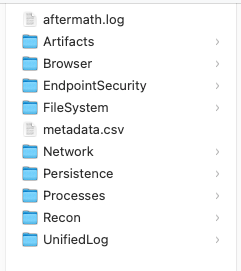
For example, within the Persistence file, we could see a bunch of different launch items. Each item had the binary's SHA256 hash attached allowing you to confirm the binary was the expected binary on a service like VirusTotal.
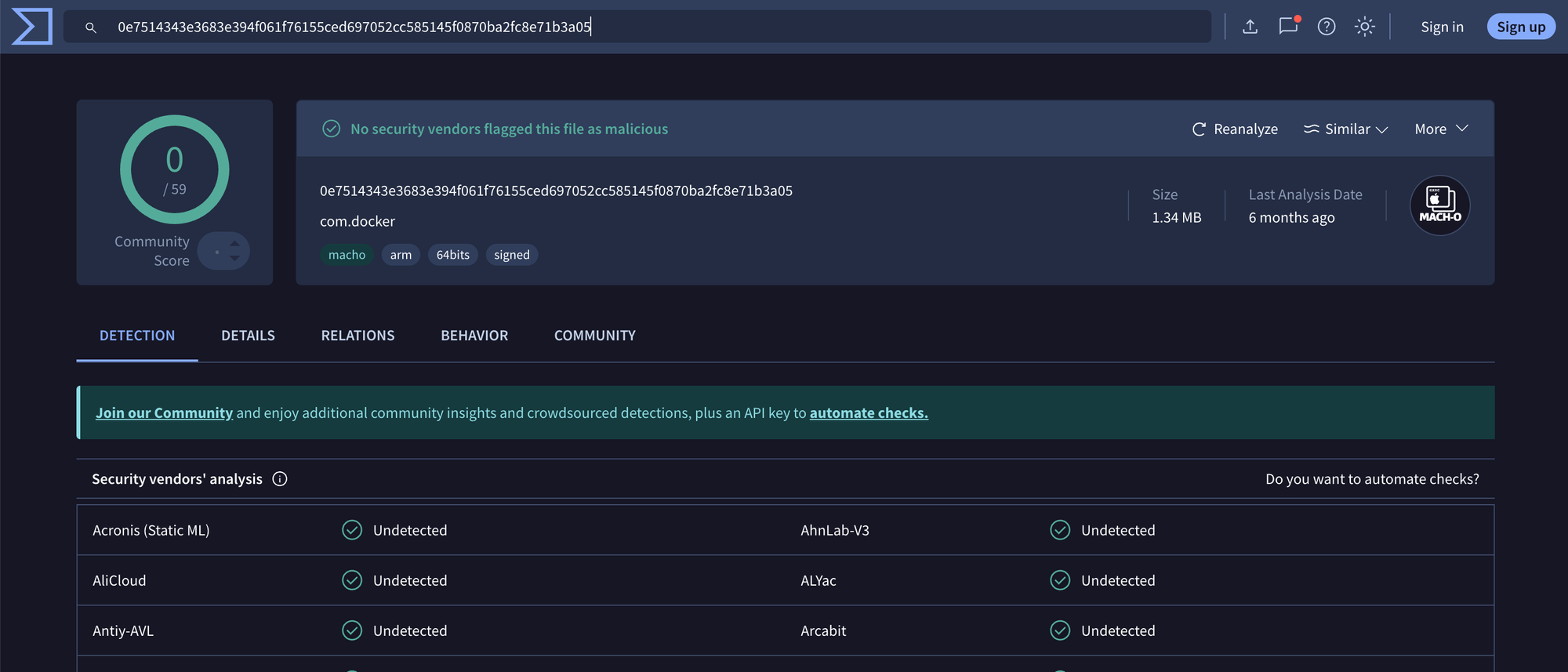
Here is an example of follow-up that you may commit.
My understanding is that Aftermath can be integrated with services like Jamf (an Apple Device Management System) or SIEMs (such as Splunk or LogRhythm). However, there is no existing GUI for Aftermath to speed up IR for Apple products. This could potentially be developed and I may look into it. There are a lot of potential issues, but this may be my next project.