Boss of the SOC: Web Site Defacement Scenario

I've recently been diving into various research areas, including malware analysis, malware generation, incident response, and related fields. To sharpen my skills in log analysis specifically, I did what anyone might do and googled "Log Analysis practice." This led me to a Reddit recommendation for Splunk's Boss of the SOC. I set up an account and explored it.
Reflecting on my experience, I realised I could have earned a Gold Coin from my Blue Team Level 1 certification if I'd had a better grasp of Splunk and log analysis.
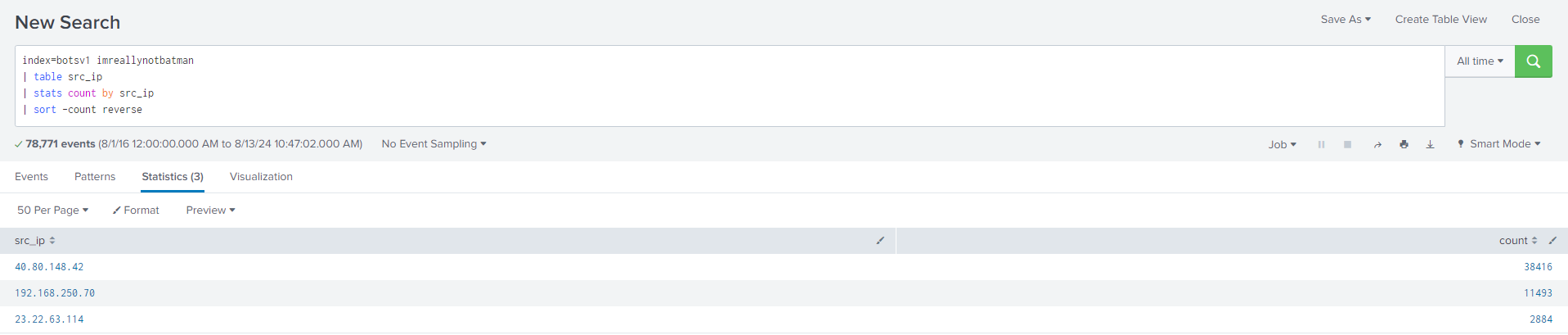
Question 101: What is the likely IPv4 address of someone from the Po1s0n1vy group scanning imreallynotbatman.com for web application vulnerabilities?
A quick search to determine the IPs interacting with imreallynotbatman.com showed me that 40.80.148.42 is likely someone scanning the site.
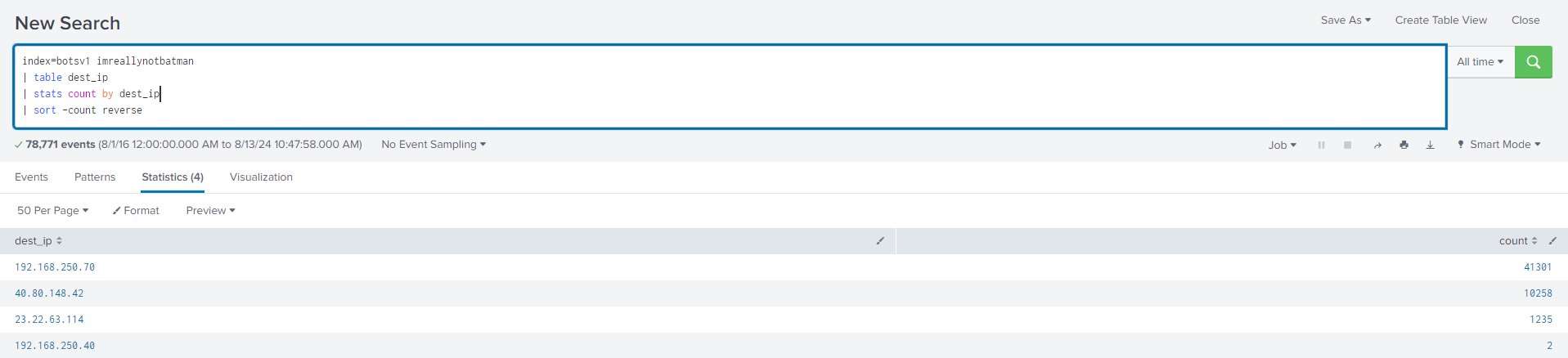
Looking at the destination IP, I deduced that imreallynotbatman.com is probably 192.168.250.70.
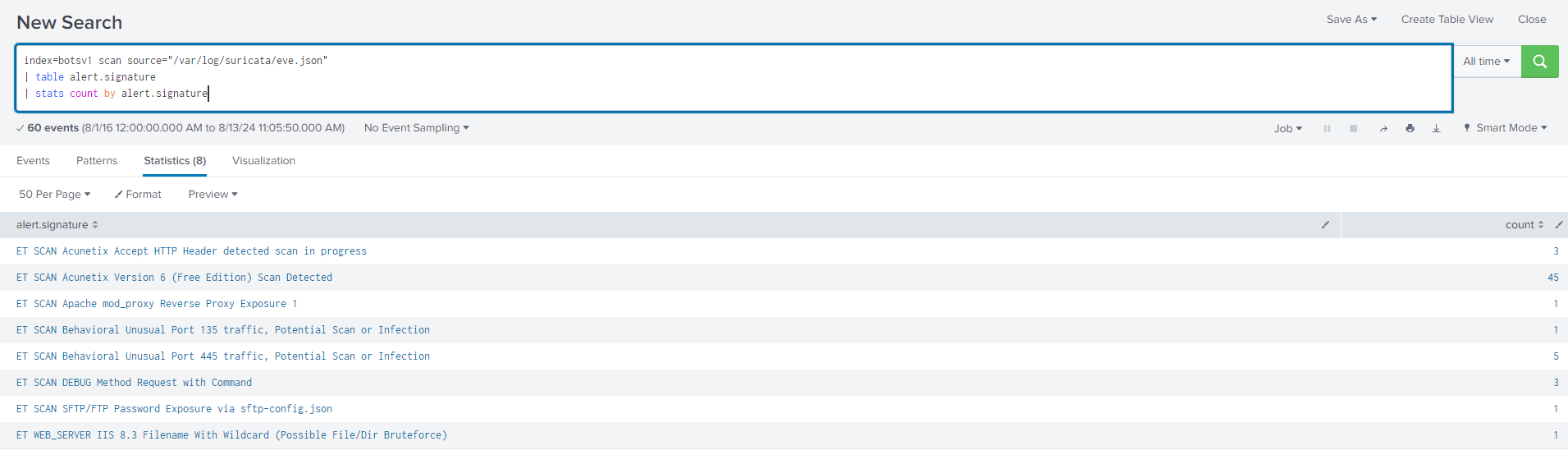
Question 102: What company created the web vulnerability scanner used by Po1s0n1vy?
For this question, I started by searching for "scan" within the Suricata logs. From there, I identified Acunetix in the alert.signatures. By creating a table showing the count, I could see all the varying alert.signatures and their frequency.
Question 103: What content management system is imreallynotbatman.com likely using?
What content management system is imreallynotbatman.com likely using? I found "Joomla" mentioned when searching for the client IP of imreallynotbatman.com along with the term "content."
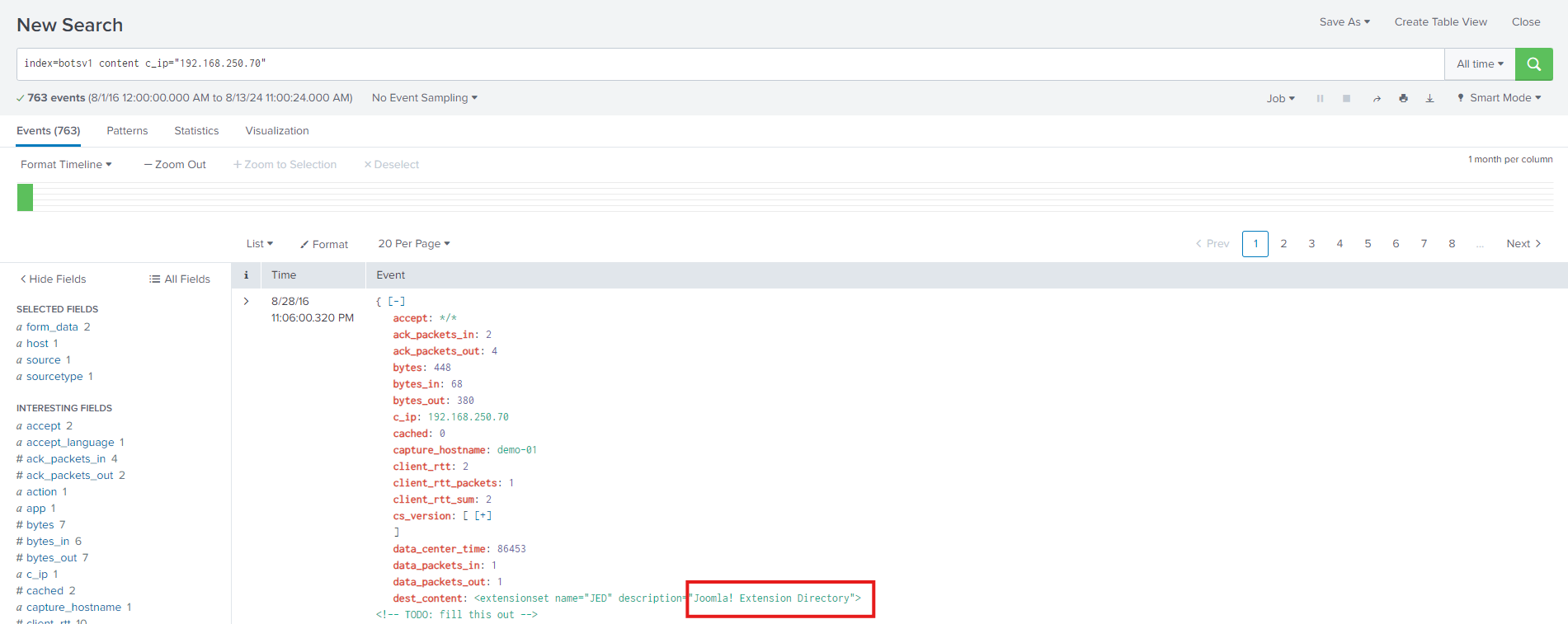
I didn't initially realise Joomla was a CMS, but a quick Google search confirmed that Joomla is a free and open-source content management system.

Question 104: What is the name of the file that defaced the imreallynotbatman.com website? Please submit only the name of the file with extension?
To find the file name and extension that defaced the website, I looked at where the imreallynotbatman IP was requesting information. Using a specific query, I saw multiple requests from the website's IP address. The giveaway was that the APT group Po1s0n1vy left their name in the filename: 'poisonivy-is-coming-for-you-batman.jpeg'.
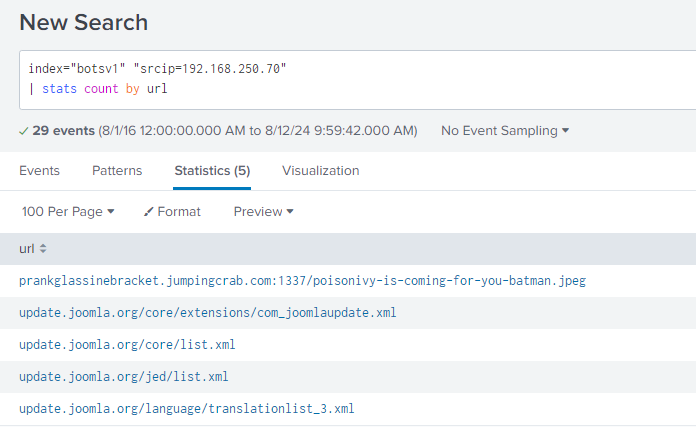
Question 105: This attack used dynamic DNS to resolve to the malicious IP. What fully qualified domain name (FQDN) is associated with this attack?
Following this we know the FQDN as it can be seen above - prankglassinebracket.jumpingcrab.com
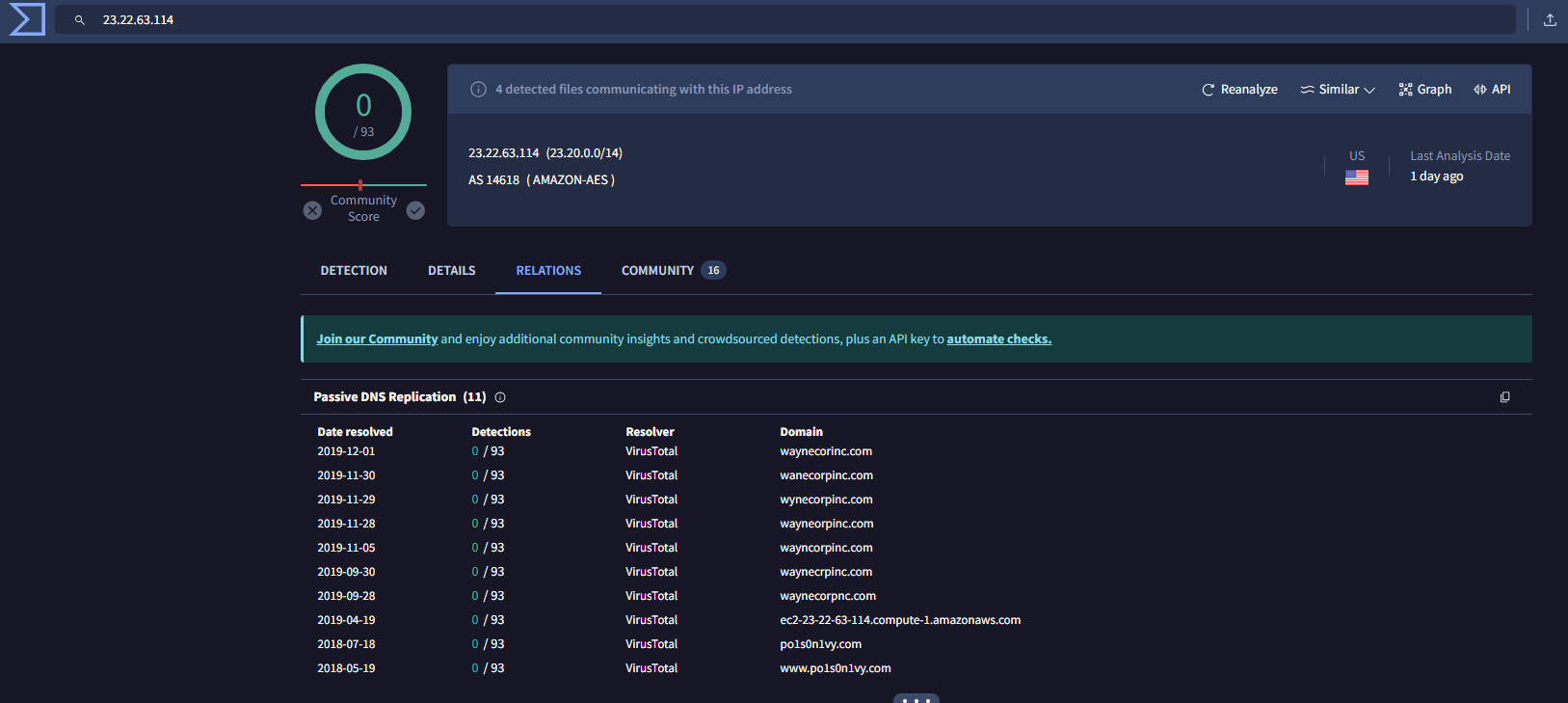
Question 106: What IPv4 address has Po1s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
We know 40.80.140.42 committed the scanning and 23.22.63.114 hosted the image to deface imreallynotbatman.com. With the use of VirusTotal, we can see 23.22.63.114 is related to Po1s0n1vy.
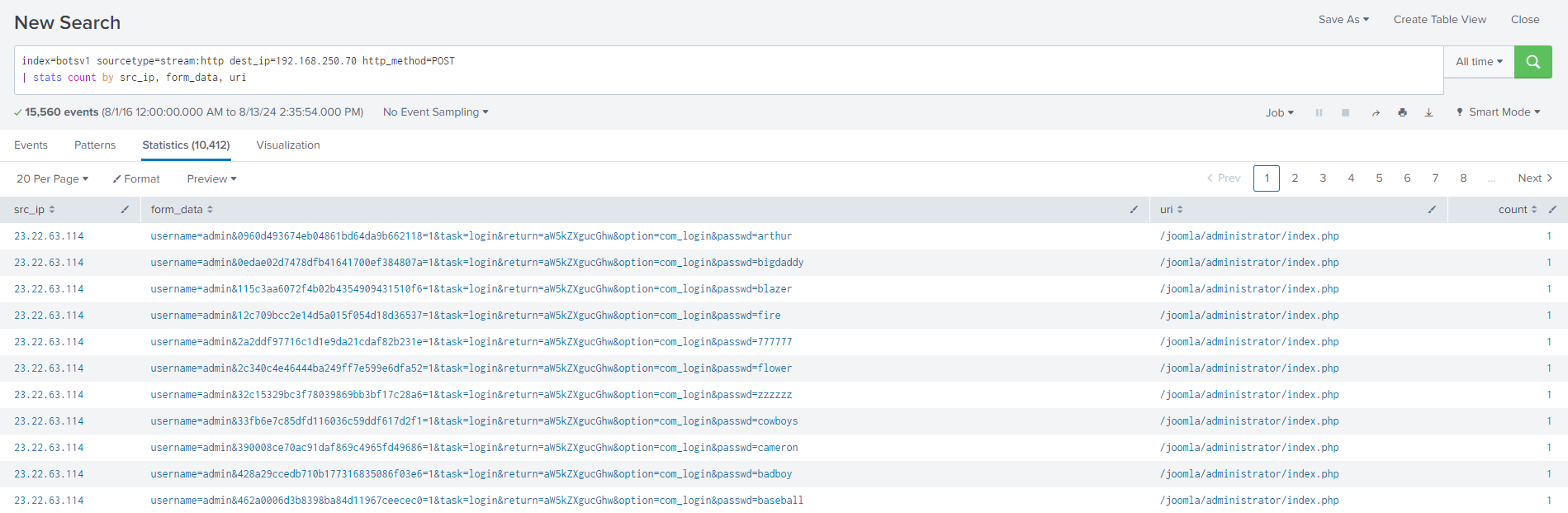
Question 108: What IPv4 address is likely attempting a brute force password attack against imreallynotbatman.com?
By searching HTTP stream data with POST requests to the destination IP of imreallynotbatman.com, I found multiple login attempts through the form data and URIs attached. These all came from a source IP of 23.22.63.144, which I identified as likely the brute force attempt.
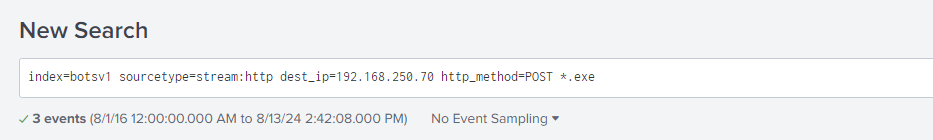
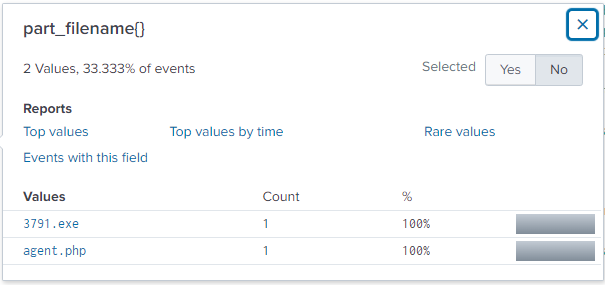
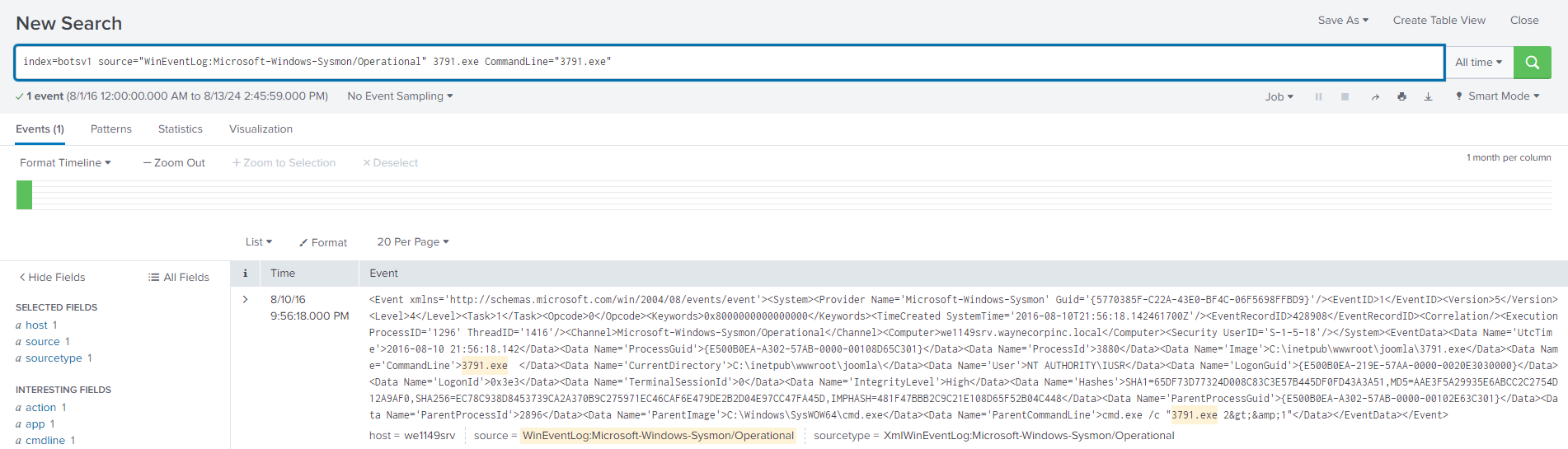
Question 109: What is the name of the executable uploaded by Po1s0n1vy?
Using a similar search to the previous query, I looked at POST requests made to the destination IP (192.168.250.70) with a wildcard search of executable files. I found a couple of filenames that raised concern, with 3791.exe being the more suspicious of the two.
Question 110: What is the MD5 hash of the executable uploaded?
Initially, I found multiple MD5 hashes for the 3791 executable.
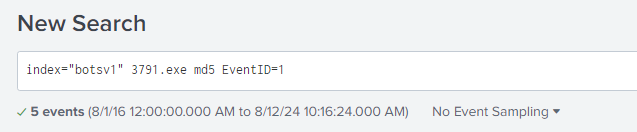
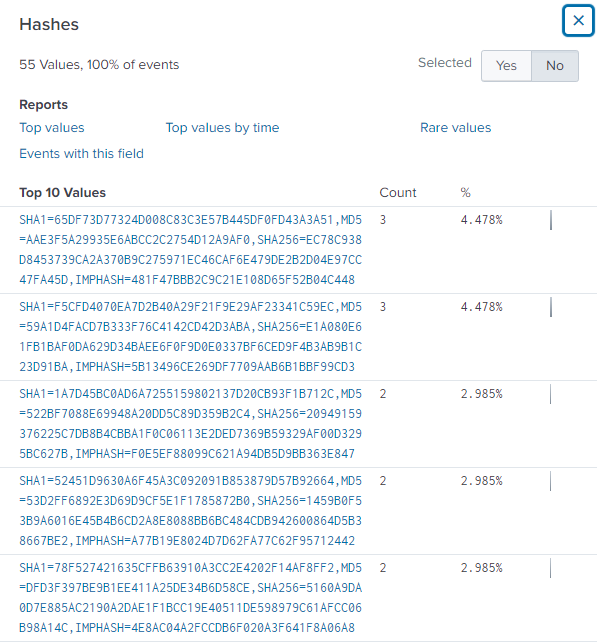
To narrow it down, I adjusted my query to search the Sysmon logs, setting the CommandLine value to 3791.exe. This left me with one MD5 hash: AAE3F5A29935E6ABCC2C2754D12A9AF0.
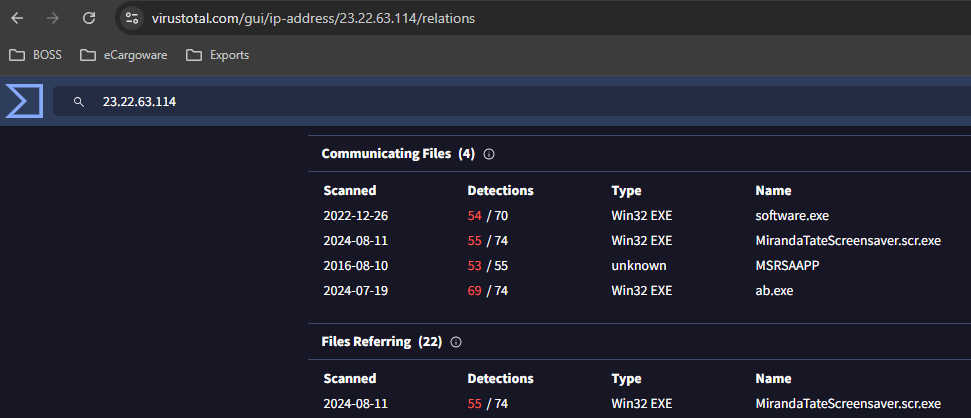
Question 111: GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the Po1s0n1vy APT group, if initial compromise fails, is to send a spear phishing email with custom malware attached to their intended target. This malware is usually connected to Po1s0n1vys initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.
With a bit of research on VirusTotal (using the IP I already knew was related to Po1s0n1vy), I found a suspicious executable 'MirandaTateScreensaver.scr.exe'.
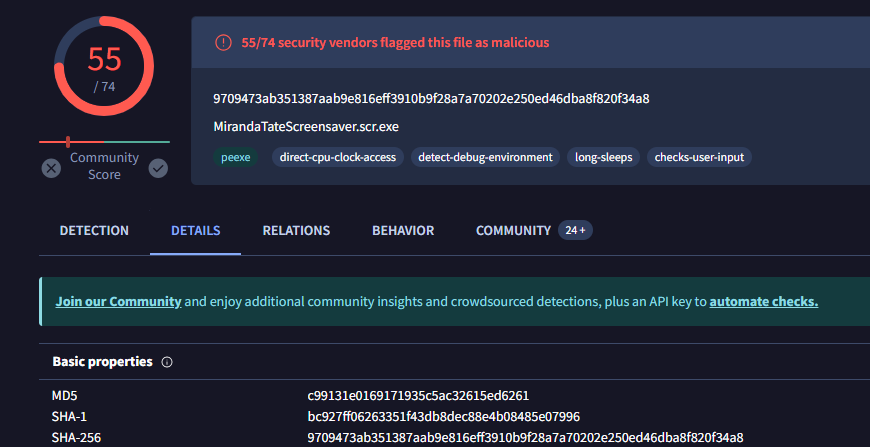
Clicking on the link, I found more information, including that the file is a trojan and its SHA256 hash: 9709473ab351387aab9e816eff3910b9f28a7a70202e250ed46dba8f820f34a8.
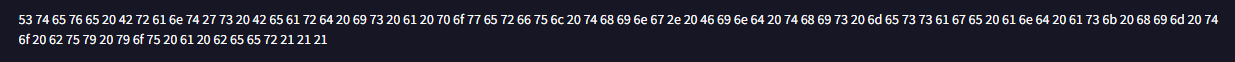
Question 112: What special hex code is associated with the customised malware discussed in question 111?
Digging deeper into the file, I found the associated hex code under the Community tab.
Question 114: What was the first brute force password used?
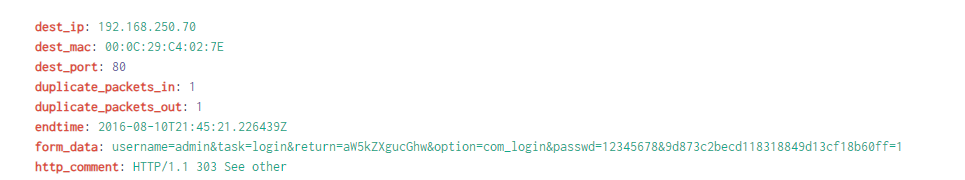
By analysing the HTTP Post requests from the targeted URI and setting the search to display events in reverse, I identified the first password used: 12345678.
Question 115: One of the passwords in the brute force attack is James Brodsky's favorite Coldplay song. We are looking for a six character word on this one. Which is it?
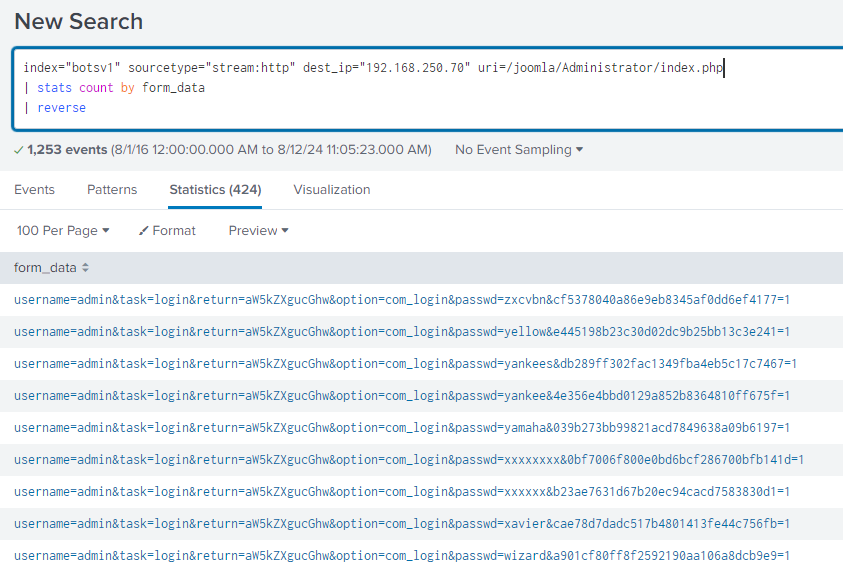
Using a similar search, I narrowed it down and, knowing a few Coldplay songs, "Yellow" was at the front of my mind. Sure enough, "Yellow" was one of the first passwords to appear when searched.
Question 116: What was the correct password for admin access to the content management system running "imreallynotbatman.com"?
Using a few more refined queries, I searched for passwords used to access the website's IP (192.168.250.70) and noticed "batman" being used twice, which implied it was successful.
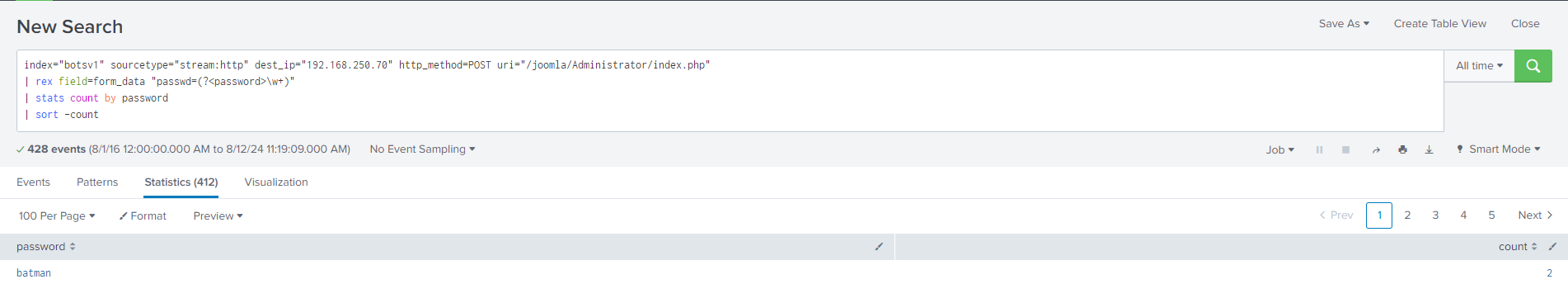
To confirm, I checked if the password also came from 40.80.148.42, the IPv4 address used for scanning web app vulnerabilities (not just the brute-forcing IP address).
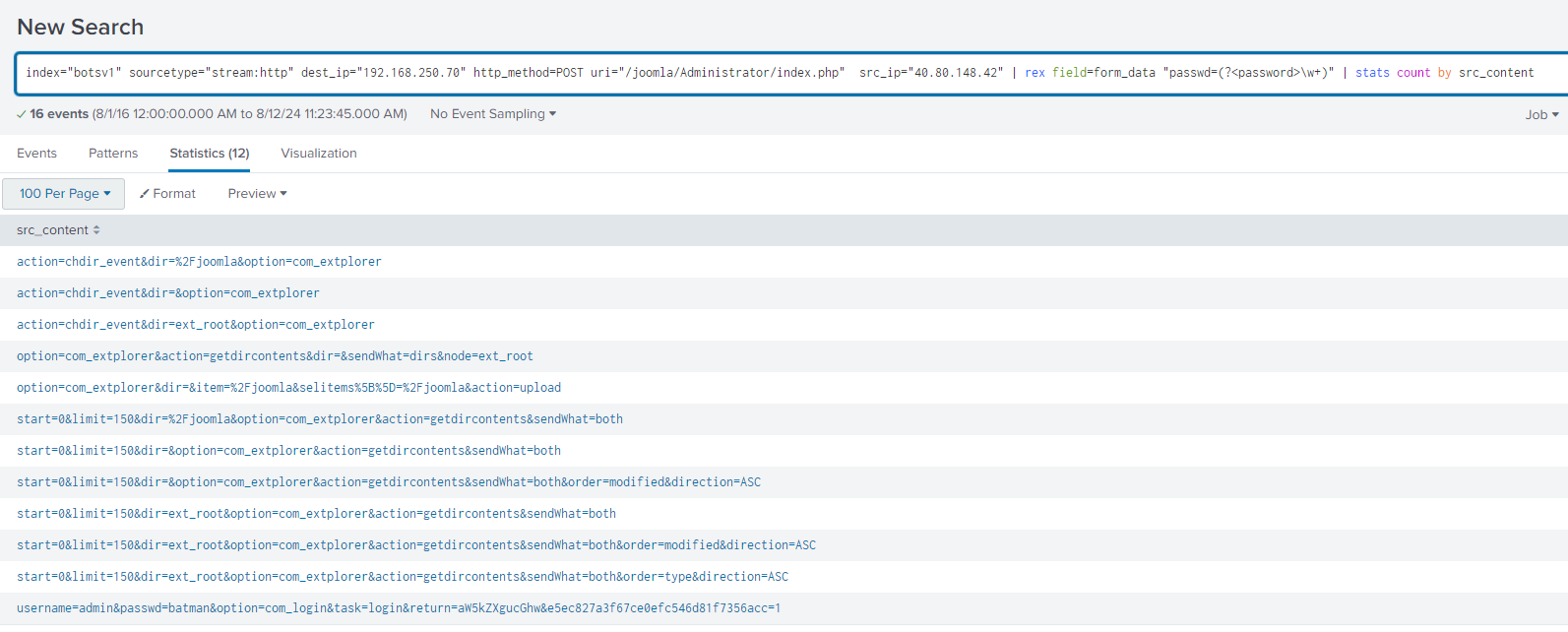
Question 117: What was the average password length used in the password brute forcing attempt?
My Splunk QL skills aren't exceptional, but I knew there had to be a way to determine the average password length using it. With a bit of help from ChatGPT, I calculated the average password length, which turned out to be 6.
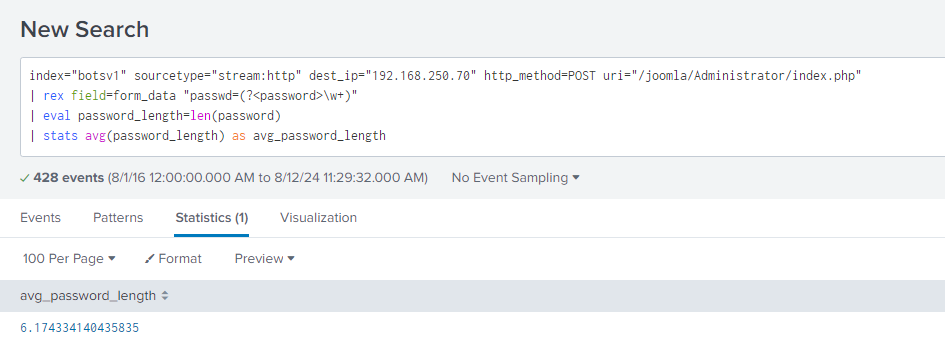
Question 118: How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login?
I used a command to look for any POST requests that included the password "batman" and used the transaction command related to password=batman. This returned a count of two events, with a duration of 92.169084 seconds between them. The question asked for this value to be rounded to two decimal places, so the final answer was 92.17 seconds.
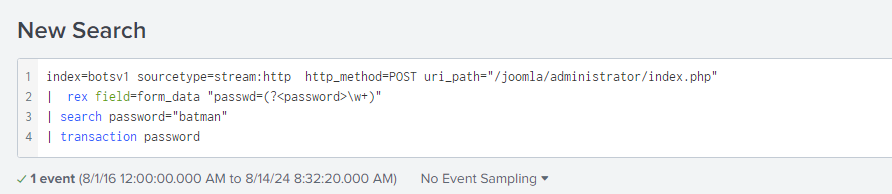
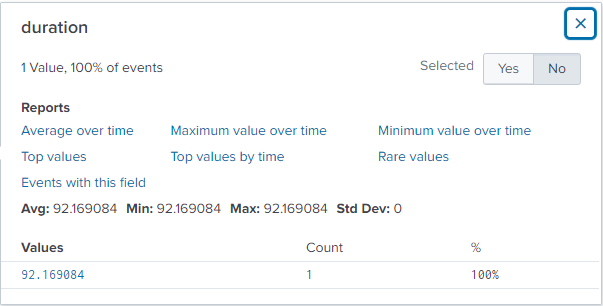
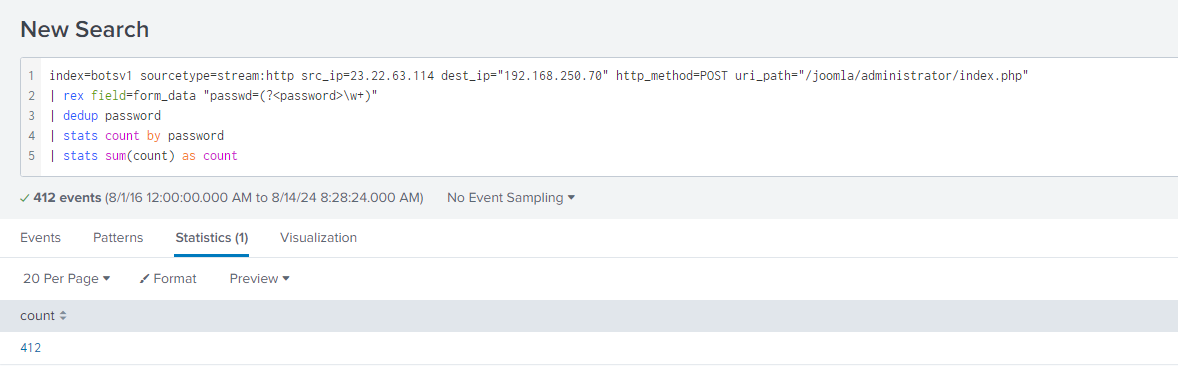
Question 119: How many unique passwords were attempted in the brute force attempt?
By searching all the attempts between the source IP of the brute forcer and the destination IP of the website, I ensured to remove any duplications and totaled the count of these passwords. The final count was 412.
All answers are in bold.
Find this scenario to run through it yourself at:
https://bots.splunk.com/